Hacktivism has evolved from grassroots digital protests to sophisticated, state-sponsored cyber operations. Check Point Research analyzed 20,000 messages from 35 hacktivist accounts using machine learning and linguistic analysis to reveal hidden connections and operational patterns. The research highlights how geopolitical events drive hacktivist activities, with groups resurfacing during crises to conduct targeted attacks. Stylometric analysis revealed clusters of hacktivist groups with overlapping linguistic fingerprints, indicating shared operators. For example, Cyber Army of Russia Reborn, Solntsepek, and XakNet form one such cluster. Understanding these operations helps improve cyber threat attribution, providing valuable insights into the evolving hacktivism landscape.
Hacktivism has undergone a remarkable transformation from its early days of digital protests to becoming a key player in state-sponsored cyber warfare. Check Point Research (CPR) provides a deep dive into this evolution, exploring how hacktivist groups, often masquerading as independent actors, are increasingly used by nation-states to conduct cyber operations. This study sheds light on the methods these groups use, their targets, and how modern attribution techniques can unveil the true operators behind the screens.
The Evolution of Hacktivism
Hacktivism’s origins trace back to the Cult of the Dead Cow, which used digital means to protest against corporations and governments. Over time, these efforts evolved into organized campaigns by groups like Anonymous, known for targeting entities such as Scientology and financial institutions. Today, the landscape is dominated by state-sponsored groups. For instance, Russian hackers launched waves of attacks on Ukrainian infrastructure during the invasion, disrupting government operations, banks, and media outlets. Ukrainian groups retaliated with cyber strikes on Russian logistics, media, and financial systems.
Iranian hacktivist groups have leaked sensitive documents from government entities, exposing internal communications and destabilizing administrative functions. Similarly, Indian infrastructure faced cyber threats from hacktivist groups during regional conflicts, affecting supply chains and financial markets. These examples underscore how hacktivism has evolved into a geopolitical weapon.
Unveiling the Actors Behind the Screens
In 1996, two FBI agents knocked on the door of a remote Montana cabin, ending a nearly 20-year manhunt. The man they arrested, Ted Kaczynski—the Unabomber—had meticulously avoided leaving forensic evidence. What ultimately led to his capture was not a fingerprint or a stray hair, but his own words. His writing style, analyzed by experts, provided the key to linking him to the infamous manifesto that exposed his identity.
This case remains one of the most well-known examples of stylometry—the science of analyzing linguistic patterns to determine authorship. Just as forensic linguistics helped crack the Unabomber case, Check Point Research (CPR) has now applied modern stylometric techniques to cyber threat intelligence in a breakthrough approach to attribution. We analyzed writing styles to uncover hidden connections between seemingly unrelated groups. These groups, much like Kaczynski, operate behind layers of anonymity. Yet, they too leave behind linguistic fingerprints—patterns in syntax, vocabulary, and writing style—scattered across social media platforms like X and Telegram.
Check Point Research (CPR) applied these techniques to 20,000 messages from 35 hacktivist accounts, uncovering networks of coordinated operations. By analyzing their language, we identified clusters of groups that share operators, tactics, and even affiliations with state-sponsored actors. We uncovered recurring themes such as cyber attacks on critical infrastructure, data breaches from military organizations, and coordinated propaganda campaigns. Stylometric analysis not only revealed that groups like JustEvil and NoName057 shared writing styles with Cyber Army of Russia Reborn, but also pointed to shared operators and potential state sponsorship.
Beyond linking different groups, stylometry also revealed shifts in authorship within individual accounts. A striking example is the IT Army of Ukraine, which showed a distinct change in writing style around 2022. Before the Russian invasion, the account posted in Arabic, cheering for the Egyptian football team. After the invasion, its focus abruptly shifted to cyber attacks against Russia. This sudden stylistic change suggests the account was purchased, repurposed, or taken over. Similar patterns appeared in other groups, where some accounts reflected multiple authors, while others maintained a consistent voice, indicating a single operator.
The Role of Geopolitics in Hacktivist Operations
Geopolitical events are a major trigger for hacktivist activities. The research demonstrated that during the Russian invasion of Ukraine, multiple hacktivist groups surfaced, launching cyber attacks almost in parallel with military operations. Ukrainian groups exposed Russian communications and disrupted key infrastructure, while Russian groups retaliated with persistent DDoS attacks on Ukrainian government systems. Similarly, the Israel-Hamas conflict saw hacktivists targeting Israeli tech firms and leaking sensitive information to undermine national security.
The study’s timeline analysis showed that hacktivist groups adapt their operations based on global events, making them unpredictable and challenging to track. The visualization of these attacks over time provided critical insights into their strategies, targets, and operational patterns.
Changes in topics of interest, which are clearly visible when analyzing the visualized timelines, can also provide valuable insights. By understanding how these topics have evolved over time and correlating this information with news and other sources, we can identify who might currently be interested in these topics and, consequently, determine the individuals or groups behind them.
Modern Attribution Techniques: A Game-Changer
Attribution in cyber threat intelligence is notoriously difficult, but this research showcased how modern techniques can bridge the gap. By combining machine learning algorithms like topic modeling and stylometric analysis for linguistic fingerprinting, CPR successfully identified connections between groups and their operators. This approach revealed that many hacktivist groups often share authors, despite using different names and platforms, pointing to centralized command structures within nation states.
The study also highlighted how changes in writing style within a single group can indicate shifts in authorship, suggesting account takeovers or reassignments within state-sponsored teams. This level of detail enhances our understanding of hacktivist operations and improves the accuracy of attribution.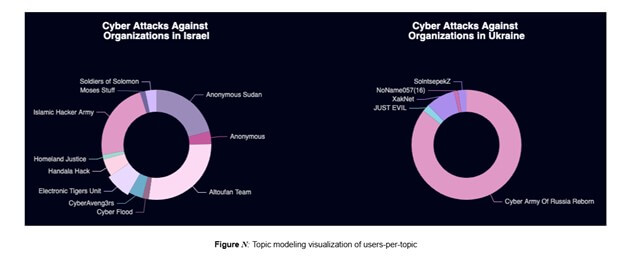
Implications for Businesses
While the primary focus of the research is on hacktivist evolution and attribution, businesses must also take note. Hacktivist operations can disrupt supply chains, leak sensitive data, and tarnish reputations. Industries such as finance, energy, and technology are particularly at risk. Adopting AI-driven threat intelligence, continuous monitoring, and employee training can help mitigate these risks.
Conclusion
The research by CPR is a significant step in understanding modern hacktivism, highlighting its evolution, key players, and the advanced techniques used for attribution. This analysis not only enhances threat intelligence but also sets the stage for future research and defense strategies in the ever-evolving cyber landscape.
As cyber criminals continue to innovate, research and security solutions must evolve in tandem to provide comprehensive protection. Businesses and government institutions alike must take proactive steps to defend against threats, leveraging advanced tools and fostering a culture of caution and awareness. Check Point Research remains committed to uncovering and mitigating these risks. By staying informed and investing in robust cyber security measures, organizations can protect their data and maintain resilience in the face of these threats.
For a comprehensive report on hacktivism, read Check Point Research’s report here.

