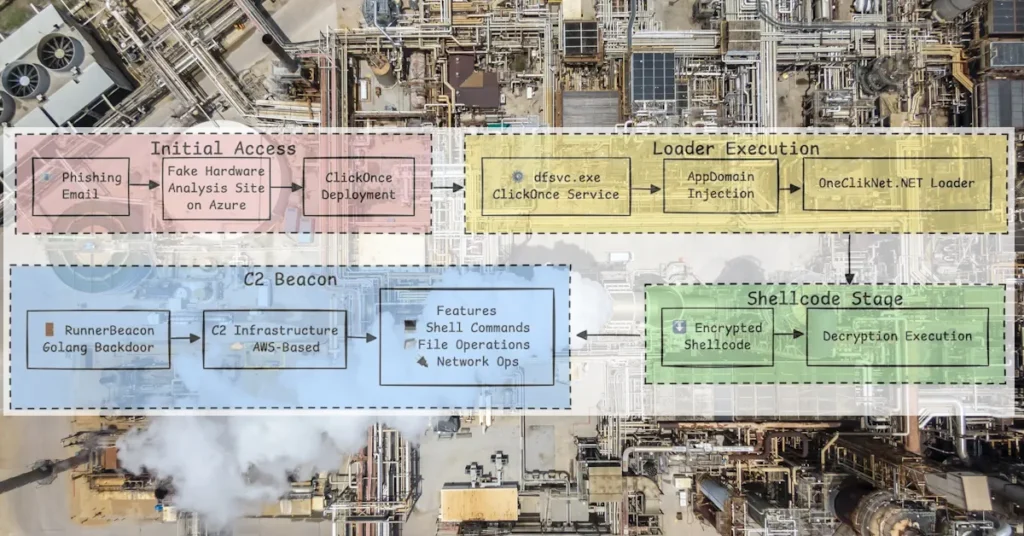
Trellix Advanced Research Center exposed a sophisticated APT malware campaign dubbed OneClik, targeting the oil and gas and energy sectors. The attackers rely on phishing and abuse of Microsoft ClickOnce to deliver payloads. While the campaign bears hallmarks of Chinese-affiliated threat actors, attribution remains tentative. OneClik reflects a broader shift toward ‘living off the land’ techniques, embedding malicious activity within legitimate cloud and enterprise tools to bypass conventional defenses.
ClickOnce is a Microsoft [dot]NET deployment technology that allows self-updating applications to install and run from remote sources. Although intended for ease of deployment, adversaries can abuse ClickOnce for stealthy code execution. The ClickOnce apps launch under the Deployment Service (dfsvc.exe), enabling attackers to proxy execution of malicious payloads through this trusted host.
“Because ClickOnce applications run with user-level privileges (no user account control required), they offer an appealing delivery mechanism for threat actors aiming to avoid privilege escalation,” Nico Paulo Yturriaga and Pham Duy Phuc, wrote in a Tuesday Trellix blog post. “In OneClik, attackers sent emails with links to a fake ‘hardware analysis’ site. Visiting the site led to a ClickOnce manifest (an .application file)—cloaked as a legitimate tool—silently downloading and executing. Once launched, the ClickOnce loader injects malicious code via [dot]NET configuration tampering.”
Specifically, they added that the loader uses AppDomainManager hijacking by crafting the [dot]exe[dot]config settings to load a remote malicious DLL at CLR startup. “This technique (AppDomainManager injection) causes the legitimate [dot]NET executable (e.g., ZSATray[dot]exe, umt[dot]exe, or ied[dot]exe) to load an attacker-controlled assembly instead of its normal dependencies. With the loader in place, payload execution proceeds under dfsvc[dot]exe, blending with benign ClickOnce activities.”
The stealthy operation unfolds across three distinct variants (v1a, BPI-MDM, and v1d), each using a [dot]NET-based loader to deploy a sophisticated Golanguage backdoor (RunnerBeacon) that communicates with threat actor infrastructure hidden behind legitimate AWS cloud services (CloudFront, API Gateway, Lambda). This makes network-based detection nearly impossible without decryption or deep behavioral analysis.
“Our analysis reveals how this campaign has progressively evolved with advanced evasion tactics and C2 obfuscation across each variant,” according to Yturriaga and Pham Duy Phuc. “Key findings include abuse of ClickOnce to proxy execution, early injection via [dot]NET AppDomainManager hijacking, and anti-analysis measures (anti-debugging loops and sandbox detection).”
Across three observed variants, the OneClik campaign employs layered anti-analysis and evasion techniques.
In the v1a variant, the loader manually relocates core system modules in memory to evade detection. It also disables Event Tracing for Windows (ETW) by patching EtwEventWrite and NtTraceEvent with nullifying instructions. To stay hidden, it suppresses its console window.
The BPI-MDM variant introduces a more advanced [dot]NET loader that launches a dedicated thread for continuous anti-debugging checks. It uses managed and native methods, including Debugger[dot]IsAttached, CheckRemoteDebuggerPresent, and NtQueryInformationProcess, to detect the presence of debuggers. If one is found, the malware exits immediately. These techniques align with ATT&CK technique T1622.
In the v1d variant, environment-aware checks intensify. The malicious DLL loaded by AppDomainManager performs sandbox and virtual machine fingerprinting. It calls NetGetJoinInformation and NetGetAadJoinInformation to determine if the host is domain-joined or Azure AD-joined; failing either check results in termination, a typical sandbox evasion behavior. It also queries physical memory via GlobalMemoryStatusEx, exiting on systems with less than 8 GB of RAM, a common trait in analysis environments. To hinder post-execution forensics, v1d deletes its own [dot]config file after loading.
The OneClik campaign uses legitimate AWS services, including CloudFront, API Gateway, and Lambda, to disguise its command-and-control (C2) traffic. In early stages, the malware routes beacons through CloudFront and API Gateway domains, blending malicious activity into normal cloud traffic that’s often allowlisted by enterprise networks. In later stages, it evolves to use AWS Lambda URLs as callback addresses, making the entire C2 flow appear as standard AWS communication. This tactic leverages AWS’s trust and ubiquity to evade detection, rendering traditional defenses like signature-based tools or SSL decryption largely ineffective.
Trellix also identified a variant of the RunnerBeacon loader in the Middle Eastern oil and gas sector in September 2023. This unique variant shares over 99 percent code similarity with OneClik’s RunnerBeacon component, although the delivery vector for that infection remains unknown. This prolonged presence indicates that the campaign is a long-term persistence effort, specifically targeting the energy sector (v1a and v1d variants). Notably, OneClik’s use of a [dot]NET-based loader, AppDomainManager hijacking, and in-memory decryption echoes techniques reported in Chinese APT operations.
The post also provided a summary of major overlaps in tactics, techniques, and procedures. OneClik and other campaigns, including those documented by Earth Baxia, AhnLab, and TGSoft, use [dot]NET AppDomainManager hijacking to load malicious DLLs during CLR runtime. This technique allows attackers to silently insert payloads early in the application lifecycle.
The deployment of encrypted payloads is also a common thread. Across these campaigns, attackers consistently use [dot]NET loaders to deliver Base64-encoded and AES-encrypted shellcode, enabling stealthy in-memory execution. All the operations eventually drop beacon-like backdoors that mimic Cobalt Strike behavior. These payloads support modular command execution and staged operations, allowing precise control over compromised systems.
Cloud infrastructure abuse is another shared trait. Earth Baxia’s infrastructure included Alibaba Cloud servers, while other campaigns retrieved components from AWS S3 and Alibaba endpoints. This consistent use of trusted cloud platforms for staging highlights a broader strategy of blending into legitimate traffic to avoid detection.
“Despite the strong overlap in techniques, we emphasize a cautious attribution stance,” Yturriaga and Pham Duy Phuc wrote. “We assess a possible with low-confidence link between OneClik and Chinese threat actors such as APT41. In the absence of “smoking gun” indicators, we refrain from definitively attributing OneClik to any specific threat actor or nation.”
However, understanding these overlaps is critically important for defenders. These TTPs tend to persist across campaigns, even as threat actors evolve their tooling or obfuscate their identities. By recognizing and mapping the TTPs of this campaign, such as ClickOne abuse, [dot]NET AppDomainManager hijacking, cloud-based staging, and Golang beacons, defenders can proactively harden systems, improve detection logic, and prioritize controls against clusters of behavior known to be effective in the wild.