A new multi-platform ransomware-as-a-service (RaaS) operation named VanHelsing has emerged, targeting Windows, Linux, BSD, ARM, and ESXi systems.
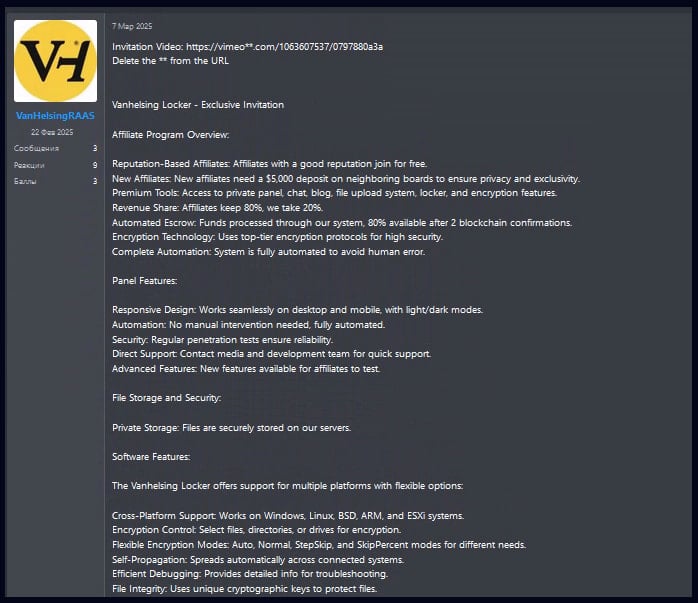
VanHelsing was first promoted on underground cybercrime platforms on March 7, offering experienced affiliates a free pass to join while mandating a deposit of $5,000 from less experienced threat actors.
The new ransomware operation was first documented by CYFIRMA late last week, while Check Point Research performed a more in-depth analysis published yesterday.
Inside VanHelsing
Check Point’s analysts report that VanHelsing is a Russian cybercrime project that forbids targeting systems in systems in CIS (Commonwealth of Independent States) countries.
Affiliates are allowed to keep 80% of the ransom payments while the operators take a 20% cut. The payments are handled via an automated escrow system that employs two blockchain confirmations for security.
Source: Check Point
Accepted affiliates gain access to a panel with full operational automation, while there’s also direct support from the development team.
Files stolen from the victims’ networks are stored directly on the VanHelsing operation’s servers, while the core team claims that they perform regular penetration tests to ensure top-notch security and system reliability.
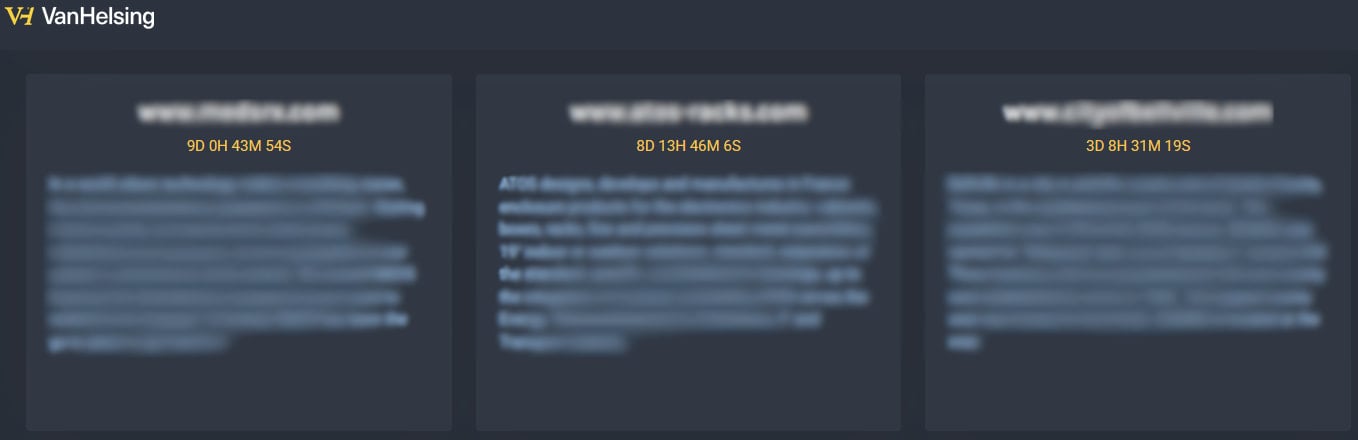
Currently, the VanHelsing extortion portal on the dark web lists three victims, two in the U.S. and one in France. One of the victims is a city in Texas, while the other two are technology companies.
Source: BleepingComputer
The ransomware operators threaten to leak the stolen files in the coming days if their financial demands aren’t met. According to Check Point’s investigation, that’s a $500,000 ransom payment.
.jpg)
Source: Check Point
Stealth mode
The VanHelsing ransomware is written in C++, and evidence suggests that it was deployed in the wild for the first time on March 16.
VanHelsing uses the ChaCha20 algorithm for file encryption, generating a 32-byte (256-bit) symmetric key and a 12-byte nonce for each file.
These values are then encrypted using an embedded Curve25519 public key, and the resulting encrypted key/nonce pair is stored in the encrypted file.
VanHelsing partially encrypts files larger than 1GB in size, but runs the full process on smaller files.
The malware supports rich CLI customization to tailor attacks per victim, such as targeting specific drives and folders, restricting the scope of encryption, spreading via SMB, skipping shadow copies deletion, and enabling two-phase stealth mode.
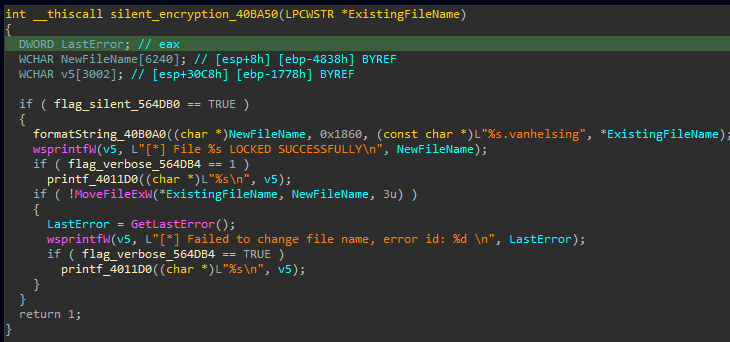
In normal encryption mode, VanHelsing enumerates files and folders, encrypts the file contents, and renames the resulting file appending the ‘.vanhelsing’ extension.
In stealth mode, the ransomware decouples encryption from file renaming, which is less likely to trigger alarms because file I/O patterns mimic normal system behavior.
Source: Check Point
Even if security tools react at the start of the renaming phase, on the second pass, the entire targeted dataset will have been already encrypted.
While VanHelsing appears advanced and quickly evolving, Check Point noticed a few flaws that reveal code immaturity.
These include mismatches in the file extension, errors in the exclusion list logic that may trigger double encryption passes, and several unimplemented command-line flags.
Despite the presence of errors, VanHelsing remains a worrying rising threat that appears that could start gaining traction soon.


