New Batavia spyware targets Russian industrial enterprises

Since March 2025, fake contract emails have been spreading Batavia spyware in targeted attacks on Russian organizations.
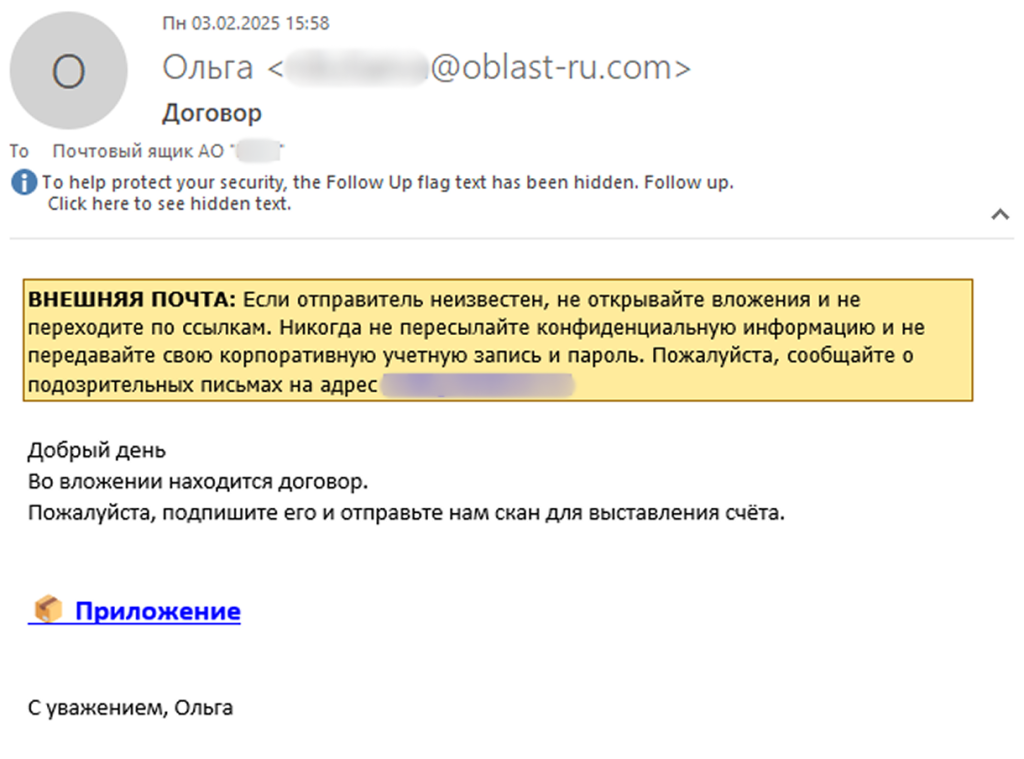
Since March 2025, a targeted phishing campaign against Russian organizations has used fake contract-themed emails to spread the Batavia spyware, a new malware designed to steal internal documents. The attack, ongoing since July 2024, begins with links to malicious .vbe files disguised as contracts or attachments. The malware includes a VBA script and two executables, detected by Kaspersky as Trojan.Batavia variants.
“Since early March 2025, our systems have recorded an increase in detections of similar files with names like договор-2025-5.vbe, приложение.vbe, and dogovor.vbe (translation: contract, attachment) among employees at various Russian organizations.” reads the report published by Russian cybersecurity firm Kaspersky. “The targeted attack begins with bait emails containing malicious links, sent under the pretext of signing a contract.”

Clicking the link included in the phishing messages downloads a VBE script that collects system info and retrieves a malware file (WebView.exe) from the attacker’s domain. The script checks the OS version to decide how to execute the payload and sends data to the command-and-control (C2) server. The attack uses tailored parameters per email to manage infection stages and evade detection.
In the second stage of the attack chain, the WebView.exe malware (written in Delphi) downloads and displays a fake contract, then begins spying on the infected system. It collects system logs, office documents, and periodically captures screenshots, sending them to a new C2 server. To avoid duplicate uploads, it hashes each file. It also downloads a new malware stage (javav.exe) and sets a startup shortcut to launch it on reboot, continuing the infection cycle.
In the last stage of the attack chain, the malware javav.exe, written in C++, expands on previous stages by targeting more file types (e.g. images, emails, presentations, archives) and exfiltrating them to a C2 server using an updated infection ID (2hc1-...). It can now change its C2 address and download/execute new payloads (windowsmsg.exe) using a UAC bypass via computerdefaults.exe. Communication with the C2 is encrypted, and the malware continues to avoid duplicate uploads by hashing files. According to Kaspersky, this stage introduces flexibility and persistence to facilitate further malicious activity.
The researchers noticed that the victims of the Batavia spyware campaign were Russian industrial enterprises. Kaspersky’s telemetry data shows that more than 100 users across several dozen organizations received the phishing messages.
“It’s also worth noting that the initial infection vector in this campaign is bait emails. This highlights the importance of regular employee training and raising awareness of corporate cybersecurity practices.” concludes the report.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Batavia spyware)