According to the latest advisory by Cert-In, 78 vulnerabilities have been discovered across a broad range of Microsoft products, including Windows, Azure, MS Office, Developer Tools, Microsoft Apps, System Center, Dynamics, and even legacy products receiving Extended Security Updates (ESU). These flaws pose serious security threats, as they can be exploited by attackers to gain restricted access, steal sensitive data, bypass critical security controls, run malicious code remotely, or launch DoS and spoofing attacks. If left unpatched, these high-risk vulnerabilities could severely compromise organizational IT infrastructure and data security.
Microsoft Software – High-Risk Vulnerabilities
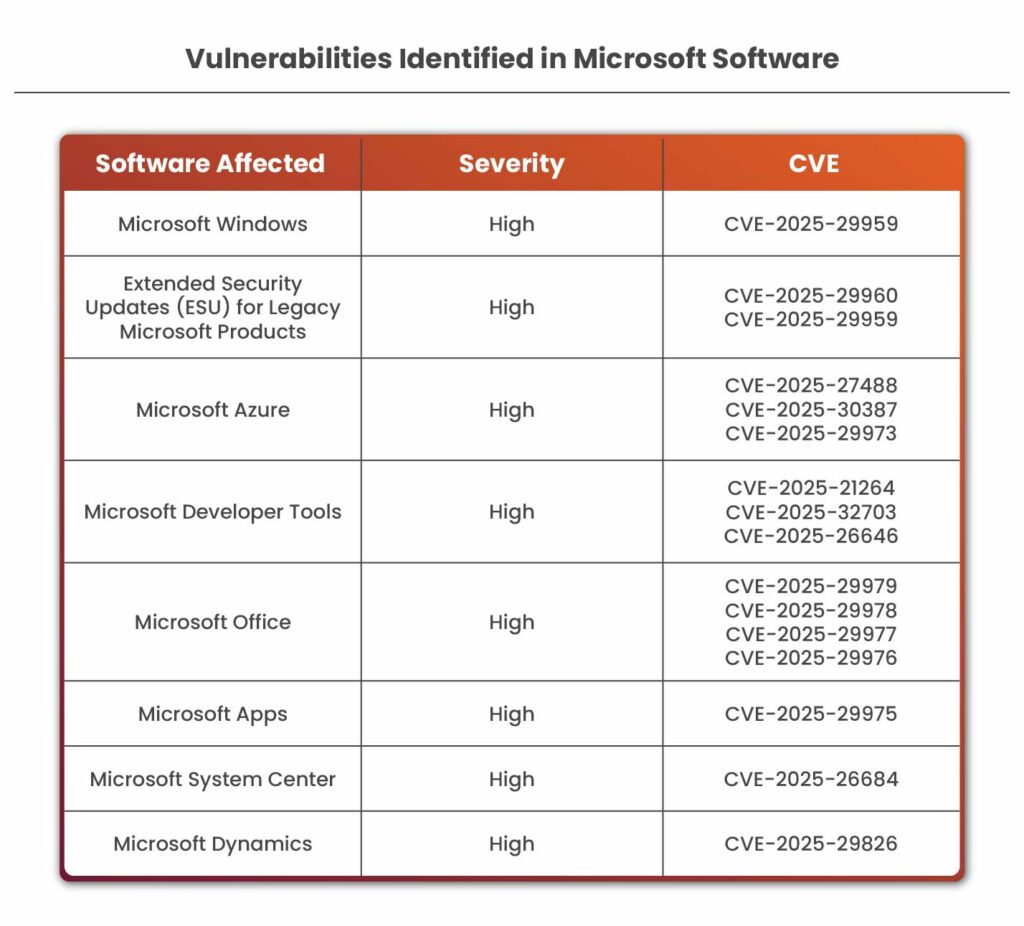
Out of the 78 flaws, the high-risk security issues that were found in various Microsoft products can allow attackers to break into your IT infrastructure, steal information, or take control of devices if not fixed quickly.
Microsoft Windows has a major flaw (CVE-2025-29959) that could let attackers run harmful programs, steal data, crash systems, or gain more control than they should.
Older Microsoft products that still receive special security updates, called Extended Security Updates or ESU, are affected by two issues (CVE-2025-29960 and CVE-2025-29959). These could allow hackers to take control, see private data, or disrupt services.
Microsoft Azure is affected by three vulnerabilities (CVE-2025-27488, CVE-2025-30387, CVE-2025-29973). These flaws could let attackers raise their access level and perform unauthorized actions.
Microsoft Developer Tools have three flaws (CVE-2025-21264, CVE-2025-32703, CVE-2025-26646) that could allow attackers to trick systems, bypass protections, or view private information.
MS Office has four major issues (CVE-2025-29979, CVE-2025-29978, CVE-2025-29977, CVE-2025-29976). The following could let attackers run harmful code or gain more control.
Microsoft Apps have one flaw (CVE-2025-29975) that could allow unauthorized access or changes.
Microsoft System Center and Microsoft Dynamics each have one serious vulnerability (CVE-2025-26684 and CVE-2025-29826) that could allow attackers to take control with elevated privileges.
Impact of the Identified High-Risk Vulnerabilities in Microsoft Software
The following are the risks associated with the Microsoft products if the vulnerabilities identified are not patched:
- Microsoft Windows – Elevation of Privilege, Remote Code Execution, Information Disclosure, Denial of Service, Security Feature Bypass
- Extended Security Updates (ESU) for Legacy Microsoft Products – Elevation of Privilege, Information Disclosure, Denial of Service, Remote Code Execution
- Microsoft Azure – Elevation of Privilege
- Microsoft Developer Tools – Security Feature Bypass, Information Disclosure, Spoofing
- Microsoft Office – Remote Code Execution, Elevation of Privilege
- Microsoft Apps – Elevation of Privilege
- Microsoft System Center – Elevation of Privilege
- Microsoft Dynamics – Elevation of Privilege
High-Risk Vulnerabilities in Microsoft Products – Previous Cert-In Advisories in 2025
April’25 – 134 Vulnerabilities Identified
Issue Date: April 11, 2025
Risk Severity: High
Software Affected: Microsoft Windows, Extended Security Updates (ESU) for Legacy Microsoft Products, Microsoft Office, Microsoft Azure, SQL Server, Microsoft Browser, Microsoft Apps, Microsoft Dynamics, System Center
Risks: Remote Code Execution, System Instability, Sensitive Information Disclosure
March’25 – 65 Vulnerabilities Identified
Issue Date: March 16, 2025
Risk Severity: High
Software Affected: Microsoft Windows, Extended Security Updates (ESU) for Legacy Microsoft Products, Microsoft Office, and Microsoft Azure
Risks: Remote Code Execution, System Instability, Sensitive Information Disclosure
February’25 – 63 Vulnerabilities Identified
Issue Date: February 15, 2025
Risk Severity: High
Software Affected: Microsoft Azure, Microsoft Windows, Microsoft Developer Tools, Extended Security Updates (ESU) for Legacy Microsoft Products, Microsoft Office, Microsoft Mariner, Microsoft for Different Platforms, Microsoft Devices
Risks: Remote Code Execution, System Instability, Sensitive Information Disclosure
January’25 – 165 Vulnerabilities Identified
Issue Date: January 15, 2025
Risk Severity: Critical
Software Affected: Microsoft Windows, Microsoft Azure, Microsoft Browser, Microsoft Dynamics, Microsoft Tools, and Miscellaneous.
Risks: Remote Code Execution, System Instability, Sensitive Information Disclosure
Steps Recommended by Cert-In
Every individual/IT administrators/security teams responsible for maintaining and updating Microsoft products, need to make sure that they install all the important security patches released by Microsoft as well as abide by what has been mentioned in the official mitigation document of these vulnerabilities. Also, here are a few of the steps recommended by Cert-In to keep your organization’s security defenses strong:
- Install the latest security updates: Make sure your Microsoft products are up to date with Microsoft’s May 2025 security patches. These updates fix known problems that hackers could use to break in.
- Watch for unusual activity and follow good security habits: Keep an eye on your systems for anything strange, like unexpected logins or unknown programmes running. Also, make sure only the right people have access to important data and that all devices (like laptops or servers) are protected with strong security tools.
- Get help from security experts: If you’re unsure, talk to cybersecurity professionals. They can help check your IT infrastructure for weak spots and make sure you have the right protection in place.
Join our weekly newsletter and stay updated
How Can Kratikal Help?
Let’s understand with a hypothetical case scenario:
CASE SCENARIO –
Industry: BFSI (Banking, Financial Services & Insurance)
Employees: 500+
IT Environment: Microsoft Windows servers, Microsoft Office 365, Azure Cloud, Microsoft Dynamics for CRM, Microsoft System Center for endpoint management
Before the Attack: Unpatched Vulnerabilities Ignored
In May 2025, CERT-In released its 5th advisory of the year, listing 78 vulnerabilities in various Microsoft products. Despite the advisory, the internal IT team at the organization delayed patching due to operational workload and assumed their antivirus and firewall would suffice. The following vulnerabilities were left unpatched:
- CVE-2025-29959 (Windows – Remote Code Execution)
- CVE-2025-29979 (Microsoft Office – RCE via malicious document)
- CVE-2025-29973 (Azure – Elevation of Privilege)
Thus, resulting in an exploit path:
The attacker found an open Remote Desktop (RDP) port on one of the organization’s older Windows servers that hadn’t been updated. They used a known flaw (CVE-2025-29959) to break in and take control of the server. From there, they used another weakness in Microsoft Azure (CVE-2025-29973) to get more access and move around the company’s systems, eventually reaching other computers and stealing sensitive data.
How Kratikal Could Have Helped Prevent This Attack Scenario
Kratikal can help organizations prevent such attacks by performing Vulnerability Assessment and Penetration Testing. VAPT helps identify security flaws and along with its risk severity. Cybersecurity companies like Kratikal then provide comprehensive patching recommendations to the testing organization’s security team.
Here’s how Kratikal performs VAPT:
- Information Gathering: We collect comprehensive details on your network architecture, devices, and communication protocols.
- Planning & Analysis: We create a customized testing strategy designed to simulate real-world attacks with minimal impact on operations.
- Vulnerability Detection: We scan your infrastructure using industry-leading tools to identify and prioritize security weaknesses.
- Penetration Testing: Our experts manually exploit critical vulnerabilities, including custom tests aligned with your business logic.
- Reporting: We provide a detailed report outlining vulnerabilities, their severity, proof of concepts, and remediation steps.
- Patch Recommendations: We review findings with your team and offer practical guidance on how to remediate and strengthen defenses.
- Re-Testing: We conduct follow-up tests to verify all vulnerabilities are properly patched and no new risks exist.
How Kratikal Can Help in Case a Cyberattack Happened
Let’s understand it with remote code execution. In case of RCE, conducting a Root Cause Analysis (RCA) is essential to understand how the vulnerability occurred in the first place. RCA helps identify the exact weakness, such as a coding error, missing security patch, poor input validation, or misconfiguration, that allowed the attacker to execute code remotely. By uncovering the root cause, organizations can fix the underlying issue, improve their security controls, and prevent similar vulnerabilities in the future.
Approach for Conducting RCA by Kratikal
- Immediate Action: At Kratikal, our top priority is to respond quickly to any ongoing cyberattack. We act fast to control the situation and reduce the damage. Our team immediately puts protective measures in place to stop the attack from spreading or causing more harm.
- Thorough Investigation: We carefully study how the affected application is built to understand where the risks are. During code reviews, we focus on the most dangerous threats and give special attention to the organization’s critical applications. These are assessed in detail to find and rank the most serious vulnerabilities.
- Detailed Reporting: Kratikal prepares in-depth reports that explain every step we took during the investigation. From the first action we took to identifying warning signs (also known as Indicators of Compromise), our reports clearly show what happened, when, and how. This gives a complete overview of the attack and helps everyone understand it better.
- Evidence and Proof: We provide solid proof of the attack, which helps confirm our findings. This includes logs, screenshots, or any other data that shows what the attacker did. It builds trust and helps show how serious the situation is and why our recommended actions matter.
- Comprehensive Recommendations: We don’t just point out what went wrong; we also suggest exactly what should be done to fix it and avoid similar problems in the future. Our recommendations are customized to the specific weaknesses found during the incident, helping to improve overall security.
FAQs
- What are the latest high-risk vulnerabilities found in Microsoft software?
These issues include risks like remote code execution, elevation of privilege, and information disclosure, which can allow attackers to gain unauthorized access or control if not patched immediately.
- How can unpatched Microsoft vulnerabilities affect your organization?
If left unpatched, these Microsoft vulnerabilities can lead to data breaches, system takeovers, service disruptions, or security feature bypasses. Attackers may exploit these flaws to steal sensitive data, run malicious code remotely, or shut down critical operations.
The post Multiple High-Risk Vulnerabilities in Microsoft Products appeared first on Kratikal Blogs – Information Hub For Cyber Security Experts.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs – Information Hub For Cyber Security Experts authored by Puja Saikia. Read the original post at: https://kratikal.com/blog/multiple-high-risk-vulnerabilities-in-microsoft-products/


