Cyber criminals continue to innovate, with a recent innovation involving the hijacking of expired Discord vanity invite links to silently deliver malicious payloads. This new campaign, discovered by Check Point Research, delivers AsyncRAT, now ranked number 3 among Top Malware for June. Using trusted platforms such as GitHub, Bitbucket, and Discord for payload delivery and data exfiltration, the attackers have devised an advanced multi-stage malware delivery system, including ClickFix phishing tactics and ChromeKatz to bypass encryption mechanisms. These developments underscore the ever-evolving nature of cyber threats, with SafePay remaining a top ransomware threat and the education sector continuing to face significant risks.
AsyncRAT Campaign Exploits Discord to Deliver Malware
Check Point Research has uncovered a sophisticated campaign delivering AsyncRAT via expired Discord invite links. This innovative attack tactic bypasses traditional security mechanisms, using trusted platforms to stealthily deliver the malware and exfiltrate data. The attackers also deploy a customized Skuld Stealer targeting crypto wallets, alongside multi-stage loaders to evade detection. This method of using trusted services, combined with time-based evasions, highlights the increasing sophistication of cyber criminal tactics.
Top Malware Families in June 2025
FakeUpdates is the most prevalent malware this month with an impact of 4% worldwide organizations, followed by Androxgh0st with an impact of 3% and AsyncRat with 2% impact.
*The arrows relate to the change in rank compared to the previous month.
- ↔ FakeUpdates – Fakeupdates (AKA SocGholish) is a downloader malware that was initially discovered in 2018. It is spread through drive-by downloads on compromised or malicious websites, prompting users to install a fake browser update. Fakeupdates malware is associated with a Russian hacking group Evil Corp and used to deliver various secondary payloads after the initial infection.
- ↑ Androxgh0st – AndroxGh0st is a Python-based malware that targets applications using the Laravel PHP framework by scanning for exposed .env files containing sensitive information such as login credentials for services like AWS, Twilio, Office 365, and SendGrid. It operates by utilizing a botnet to identify websites running Laravel and extracting confidential data. Once access is gained, attackers can deploy additional malware, establish backdoor connections, and exploit cloud resources for activities like cryptocurrency mining.
- ↑ AsyncRat – AsyncRAT is a remote access Trojan (RAT) targeting Windows systems, first identified in 2019. It exfiltrates system information to a command-and-control server and executes commands such as downloading plugins, terminating processes, capturing screenshots, and updating itself. Commonly distributed via phishing campaigns, it is used for data theft and system compromise.
- ↑ Formbook – Formbook, first identified in 2016, is an infostealer malware that primarily targets Windows systems. The malware harvests credentials from various web browsers, collects screenshots, monitors and logs keystrokes, and can download and execute additional payloads. The malware spreads via phishing campaigns, malicious email attachments, and compromised websites, often disguised as legitimate files.
- ↓ Remcos – Remcos is a remote access Trojan (RAT) first observed in 2016, often distributed through malicious documents in phishing campaigns. It is designed to bypass Windows security mechanisms, such as UAC, and execute malware with elevated privileges, making it a versatile tool for threat actors.
- ↔ AgentTesla – AgentTesla is an advanced RAT (remote access Trojan) that functions as a keylogger and password stealer. Active since 2014, AgentTesla can monitor and collect the victim’s keyboard input and system clipboard and can record screenshots and exfiltrate credentials entered for a variety of software installed on the victim’s machine (including Google Chrome, Mozilla Firefox and Microsoft Outlook email client). AgentTesla is openly sold as a legitimate RAT with customers paying $15 – $69 for user licenses.
- ↑ Lumma – Lumma Stealer, first detected in August 2022, is a malware-as-a-service (MaaS) information stealer that exfiltrates sensitive data from infected Windows systems, including credentials, cryptocurrency wallets, and browser information. It spreads through phishing campaigns, malicious websites, and social engineering tactics like the ClickFix method, where users are tricked into executing attacker-provided PowerShell commands.
- ↑ Amadey – Amadey is a modular botnet that emerged in 2018, primarily targeting Windows systems. It functions as both an infostealer and a malware loader, capable of reconnaissance, data exfiltration, and deploying additional payloads, including banking Trojans and DDoS tools. Amadey is primarily distributed by exploit kits such as RigEK and Fallout EK, and through phishing emails and other malware like SmokeLoader.
- ↑ Phorpiex – Phorpiex, also known as Trik, is a botnet that has been active since at least 2010, primarily targeting Windows systems. At its peak, Phorpiex controlled more than a million infected hosts. Phorpiex is notorious for distributing other malware families, including ransomware and cryptominers, via spam campaigns, and has been involved in large-scale sextortion campaigns.
- ↓ Raspberry Robin – RaspberryRobin is a worm, that first emerged in September 2021. It is primarily spread through infected USB drives and is noted for its sophisticated techniques to evade detection and establish persistence on compromised systems. Once a system is infected, Raspberry Robin can facilitate the download and execution of additional malicious payloads.
Top Ransomware Groups
Based on the latest insights from ransomware “shame sites” run by double-extortion ransomware groups that post victim information, Qilin is the most prevalent ransomware group this month, responsible for 17% of the published attacks, followed by Akira with 9% and Play with 6%.
- Qilin – Qilin, also known as Agenda, is responsible for 17% of the attacks this month. It targets large enterprises, particularly in healthcare and education, using phishing emails to exfiltrate sensitive data before encrypting it.
- Akira – Akira, emerging in early 2023, is responsible for 9% of ransomware attacks. This group exploits vulnerabilities in VPN endpoints and encrypts data with a “.akira” extension.
- Play – Play Ransomware remains a significant threat, responsible for 6% of the ransomware attacks. It targets organizations via compromised valid accounts or unpatched vulnerabilities, including Fortinet SSL VPNs.
Top Mobile Malware
The top mobile malware families for June 2025 are:
- ↔ Anubis – Anubis remains the most prevalent mobile malware, capable of bypassing multi-factor authentication (MFA), keylogging, and stealing banking credentials. It continues to be distributed through malicious apps on the Google Play Store.
- ↔ AhMyth – AhMyth is a remote access Trojan (RAT) that targets Android devices, often disguised as legitimate apps like screen recorders or games. It exfiltrates sensitive information such as banking credentials and MFA codes.
- ↑ Hydra – Hydra, a banking Trojan, climbs to third place. It requests dangerous permissions from victims to access their banking apps and steal credentials.
Top-Attacked Industries
The education sector remains the most targeted industry globally, followed by government and telecommunications. These sectors continue to face significant threats due to their critical infrastructure and large user bases.
- Education
- Government
- Telecommunications
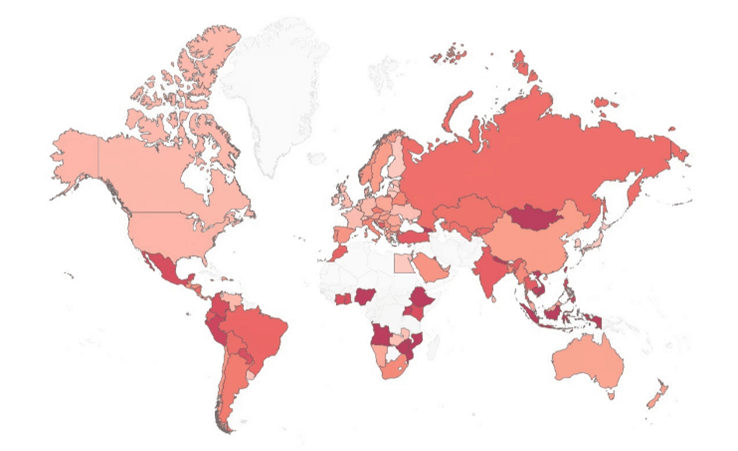
Threat Index per Country
Check Point’s global risk map for June 2025 shows heightened malware activity in regions such as Eastern Europe and Latin America, with a particular rise in FakeUpdates and Phorpiex infections. In Asia, countries like Nepal and Vietnam report increased attacks involving Remcos and AgentTesla. Western Europe sees a surge in Lumma Stealer and Raspberry Robin infections, especially in Spain and France.
Conclusion
June’s data highlights the growing sophistication of multi-stage malware campaigns, with new threats like the AsyncRAT campaign using trusted platforms to evade detection. As FakeUpdates remains widespread, Qilin emerges as a top ransomware threat, with its impact on large enterprises, especially in healthcare and education. The education sector continues to be highly targeted, underscoring the need for strong, proactive security measures to counteract these evolving threats.
Recommendations and Defensive Actions
Organizations must prioritize a prevention-first approach, including anti-phishing training, regular patching, and robust threat prevention solutions. Check Point’s Threat Emulation and Harmony Endpoint offer real-time protection against these increasingly sophisticated cyber threats.