Even the best-equipped SOC teams bleed time on two fronts:
Tier 1 analysts click through false positives all day.
Tier 2 analysts correlate logs, pivot across tools and write reports long after business hours.
“Tier 1 and Tier 2 is your primary work within a security operations center, so anything you can do to drive efficiency gains is a huge positive,” says Philip Beck, former SOC manager and now D3’s Director of Sales Engineering, in our recent Morpheus AI workshop. Our new whitepaper, “Fully Automate L1 & L2 SOC Ops—This Is How We Do It” explains the architecture behind those wins. Grab it now, then read on for a deeper dive into what those L1 and L2 tasks are, and why they’re perfect targets for autonomy.
Why Full-Stack Automation Beats Piecemeal Fixes
A 2025 Gartner survey of cybersecurity leaders found that organizations have 43 cybersecurity tools in their product portfolio, while 5% reported having 100+ tools. Tool sprawl forces analysts to manually piece together context, “ticket-fling” escalations, and ultimately, burn out while chasing ghosts.
Piecemeal automation, like legacy SOARs, only adds to the complexity with brittle scripts and endless playbook maintenance. A true autonomous SOC solution must sit above the entire security stack, unifying every signal without asking you to rip and replace the tools you already trust. Morpheus AI helps SOC teams with:
- Efficiency & Speed. A 3.5-hour phishing investigation case drops to < 2 minutes when Morpheus handles every enrichment, query, and correlation in parallel. Your team gets answers 315x faster, crushing response times.
- Scalability. Automation lets MSSPs add tenants, or enterprises add business units and new use cases, without adding headcount.
- Cost Control. “Cut the triage bill and you unlock budgets for new talent and tools,” noted Pierre Noujeim, D3’s Director of Cyber Security Services, in our recent workshop. By fully automating L1 and L2 SOC work, you can reinvest those six-figure savings into proactive security measures and upskilling your team.
- Analyst Retention. Removing “hash-check drudgery” reverses the burnout that drives two-year turnover cycles.
What are L1 and L2 SOC Tasks?
In a modern SOC, Tier-1 (L1) work is the fast-paced triage that happens the moment an alert lands: analysts ingest and normalize events from every tool, verify connector health, run quick hash / IP / URL reputation checks, enrich with asset and user context, and decide whether to close or escalate, an exercise central to day-to-day workloads. Morpheus folds each of those chores into its pre-processing pipeline, streaming alerts into a graph model, layering enrichment on the fly, and automatically dismissing about 95 percent of alerts in under two minutes.
Tier-2 (L2) work begins when something survives L1: investigators must correlate disparate signals, rebuild timelines, detonate suspect files, pivot across logs to confirm scope and root cause, and draft a containment plan. Morpheus reproduces that detective effort with its Deep Research Framework, firing dozens or even hundreds of vertical and horizontal queries at once, writing findings back into the same evidence graph, and shrinking what is typically a 3.5-hour manual investigation to roughly two minutes, complete with an AI-generated playbook and an Incident-Response Priority Score that funnels only fully scoped, high-risk incidents to Tier-3 responders.
Inside the Morpheus Engine
Morpheus AI was built to function like a world-class analyst who never sleeps, executing the entire investigation and triage workflow with superhuman speed and accuracy. Here’s how it works:
Ingestion & Unified Data Model
It starts by connecting to everything in your security stack. Morpheus’ 800+ AI-first integrations help ingest alerts and data across EDR, NDR, cloud, IAM and more. Any tool or platform with an API or webhook can be integrated with Morpheus. Instead of hoarding terabytes of data, Morpheus consumes alerts and metadata, normalizing them into a graph-based schema that preserves relationships across tools and time. Device asset tags, business-criticality, user risk scores, and threat-intel feeds are merged on the fly, giving subsequent investigation steps a 360-degree view.
Deep Research Framework (DRF)
Once an alert is ingested, Morpheus’s Deep Research Framework launches a massive, parallel investigation. It operates like a Tier 3 analyst, executing hundreds of queries across your stack in seconds, a process that takes a human analyst hours.
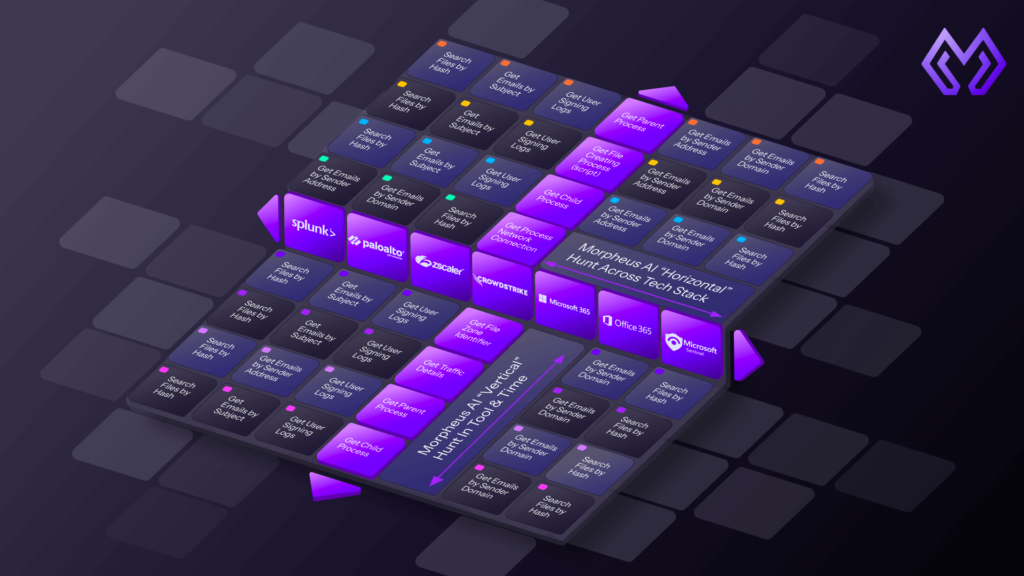
- Vertical Analysis: Dives deep into the originating tool, exploring process trees, registry keys, and raw telemetry to understand the root cause.
- Horizontal Analysis: Fans out across every integrated tool, from your firewall to your email gateway, linking related signals into a single, cohesive attack narrative.
Every investigative step is written back as a transparent, auditable YAML playbook. You don’t have to worry about black-box AI. With Morpheus, you get transparent, explainable logic that your analysts can review and refine.
Noise-Kill Automation & Continuous Learning
Alert fatigue is the enemy of an effective SOC. Morpheus’ pre-processing playbooks autonomously triage 95% of incoming alerts in under two minutes, instantly dismissing obvious false positives and low-fidelity signals. The system learns from analyst feedback. When analysts validate an incident, their thumbs-up/down decision teaches the AI, continuously refining its logic and shrinking the false-positive rate without writing new rules.

Cross-Stack Incident-Response Priority Score (IRPS)
Forget generic “high, medium, low” labels. Morpheus calculates a numeric Incident-Response Priority Score (IRPS) that blends multiple factors for true, at-a-glance prioritization:
- Threat Confidence: Reputation of IOCs, malware families, and known exploits.
- Business Impact: The criticality of the asset, data sensitivity, and potential blast radius.
- Mitigation State: Whether the user or endpoint is already contained by another tool.
- Historical Context: Previous occurrences of similar IOCs or TTPs in your environment.
The result is a perfectly sorted queue where the top item is always the most urgent threat.
Tier-3-Ready Queue
With the noise filtered and priorities set, Morpheus delivers a queue of confirmed incidents to your senior analysts. Each incident package is Tier 3-ready, complete with:
- The full attack timeline and link analysis graph.
- Root cause analysis and recommended remediation steps.
- A pre-built containment plan, with aggressive actions gated for human approval.
Analysts no longer start from scratch; they start with the answer.
Task-Level Time Savings: SOC Analyst vs. Morpheus AI
The efficiency gains are transformational. Morpheus completes a typical phishing investigation that takes an expert human analyst 3.5 hours in under two minutes.
| Task | Expert SOC Analyst | Morpheus AI |
| Alert Verification & Ticket Logging | 10 min | 5s |
| Timestamp Correlation Across Platforms | 10 min | 5s |
| Email Content and Header Analysis | 10 min | 5s |
| Extraction of Malicious URL from Email | 5 min | 5s |
| Firewall Log for Outbound Connections | 15 min | 5s |
| Network Traffic Analysis | 15 min | 5s |
| Authentication and AAD Sign-In Review | 15 min | 5s |
| User Behavior Baseline Comparison | 10 min | 5s |
| Threat Intelligence Lookup for URL/IP | 10 min | 5s |
| Domain and WHOIS Information Lookup | 5 min | 5s |
| URL Redirection and Destination Verification | 5 min | 5s |
| Endpoint Detection (EDR/Sysmon) Log Analysis | 20 min | 5s |
| Geolocation and ASN Verification | 10 min | 5s |
| User Account Activity Review | 10 min | 5s |
| Cross-Platform Log Correlation | 15 min | 5s |
| Stakeholder Notification and Escalation | 10 min | 5s |
| Containment Actions Execution | 15 min | 15s |
| Root Cause Analysis, Final Reporting | 20 min | 15s |
| Total Time | ~3.5 hours per incident | <2 minutes per incident |
Ready to Watch L1 & L2 Run on Autopilot? 
Achieve Fortune 100-level resilience without adding headcount or ripping out the tools you’ve already invested in. Morpheus delivers 100% alert coverage, 315x faster investigations, and transparent, audit-ready evidence for every action. Give your analysts their focus and their weekends back.

For more information, download our whitepaper: “Fully Automate L1 & L2 SOC Ops” →
Need to see it on your own data? Book a live demo to discuss your SOC automation challenges and automation wishlists.
The post How Morpheus AI Automates the Entire L1 & L2 Pipeline appeared first on D3 Security.
*** This is a Security Bloggers Network syndicated blog from D3 Security authored by Shriram Sharma. Read the original post at: https://d3security.com/blog/how-morpheus-ai-automates-the-entire-l1-l2-pipeline/


