At the tactical edge, Army wants 58 zero trust capabilities
CWO Four Ben Koontz, the director of the Army’s functional management office for zero trust, said a recent pilot successfully tested these cyber tools.
When it comes to the tactical edge, the Army isn’t trying to eat the zero trust apple in one bite.
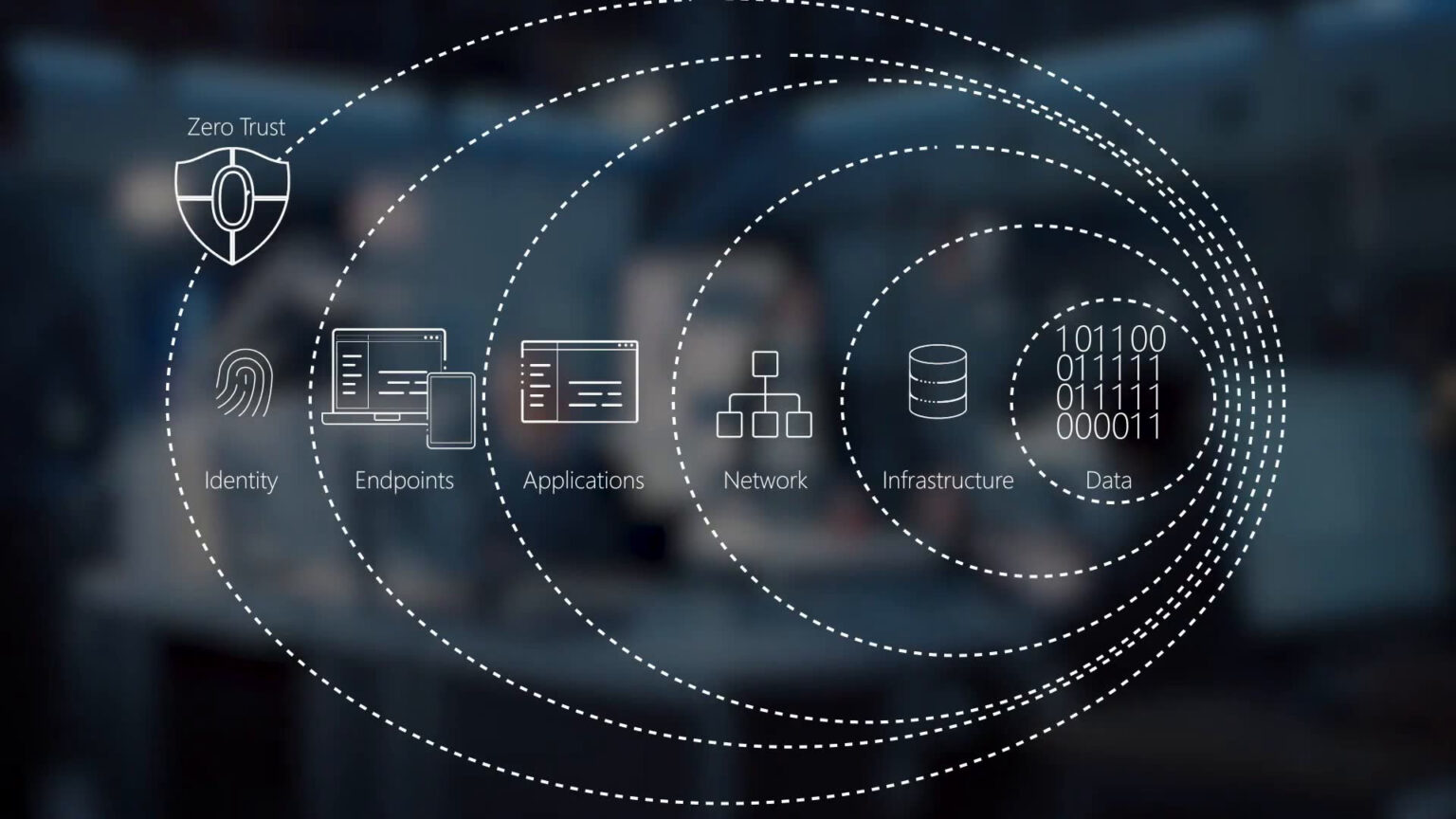
Instead of trying to make 91 different capabilities under the Defense Department’s target architecture work at the edge, the Army is focused on 58 of the most critical cyber protections.
Chief Warrant Officer Four Ben Koontz, the director of the Army’s functional management office for zero trust, said based on a gap analysis for tactical systems, the Army has begun piloting these capabilities to address their biggest cyber challenges.
“The 101st Airborne Division out of Fort Campbell already started piloting the zero trust implementation on tactical and they did very well in an assessment and a threat assessment. They’ve proved the effectiveness of it. They proved that they could take a complex topic as zero trust, architecture, design and implement it at a tactical edge and operationalize it,” said Koontz at the recent TEM 13 conference in Savannah, Georgia. “Now we’re ready at this point to develop a concept of operations and we’re developing guidance at the G6 level. We’re going to start providing that definitive guidance, and we’re going to look at getting that out in the next five to six months and start implementing zero trust across the formations in calendar year 2025.”
The new guidance will include a tactical edge zero trust strategy as well as an implementation plan. The ConOps will provide specific insights in to how to implement zero trust in the tactical formations.
“The implementation zero trust implementation guide will tell each unit how to take their current capabilities and implement zero trust with it. It’s going to almost go super in the weeds. It’s going to go very specific on step-by-step how to implement zero trust,” Koontz said. “Then the PEO is going to provide an additional document to go along with that, a cyber zero trust playbook that goes even further with quick reference guides and they’re going to provide support.”
Assessing edge implementations
Additionally, Koontz said the PEO also will create working groups to support the implementation of zero trust, who will help answer questions and track the progress of zero trust.
The Army will review implementation efforts by doing tactical edge assessments to ensure the capabilities are indeed stopping or limiting cyber attacks.
“We’ve got an assessment plan already developed, which is going to be self-assessment and what I call an operational assessment. It’s an Excel spreadsheet that has the different activities with the different capabilities,” Koontz said. “For instance, you will indicate whether the next gen firewall is configured in this manner, and this is your operational use case. There are three use cases to run through. Each division is going to do their own operational assessment, and then at another point in time, whether it’s through an Army Combat Training Center rotation or a warfighter in an Army red team will then assess them, and then we can collect the data to find out how this unit achieved X amount of zero trust activities, and this is how well they did with the red team. We can start seeing trends and seeing how well we’re doing with zero trust based on those of those assessments, from the tactical side to the enterprise side.”
Koontz said the Army released the implementation plan last year and the ConOps, along with the implementation plan and playbooks, is close to being released too.
The Army’s functional management office for zero trust worked with the Cyber Center of Excellence to develop the strategy that details the 58 capabilities.
Koontz said they brought in operational forces, cyber security experts from across the core and the division, as well as the PEO team, to figure out where the gaps exist and how to fill them.
Lessons learned from the pilot
“We’ve modularized what you can do based on what capabilities you’ve fielded. So some people may only be able to do 30 or 40, and then others will be able to do the full 58,” he said. “The 101st were chosen because they’re one of the more modernized organizations. We wanted to do the most that we could do, rather than pick one of the sub the units that hadn’t gotten everything in the pilot.”
From that pilot with the 101st, Koontz said the Army learned several important lessons.
Of course one big one is ensuring a commanders and other leaders are involved from the beginning of the planning.
Koontz said another lesson is as part of the organization’s technology baseline, they have to also understand what their network looks like and how much traffic goes through it and from where.
“As you go through the process and you start implementing these different technologies, you start hardening things and you start adding security so you have to make sure you’ve done it successfully and you’ve not taken down the environment where you stop mission command,” he said. “These mission critical weapon systems and other things, if they fail, it’s going to be very bad. So you have to ensure that because it’s such a different environment, that you can implement zero trust.”
Copyright
© 2025 Federal News Network. All rights reserved. This website is not intended for users located within the European Economic Area.