Table of Contents
As we approach the one year anniversary of two prominent ransomware group collapses (Lockbit and BlackCat/ALPHV), we find the ransomware ecosystem to be as fractured and uncertain as it did in the months following these events. The Ransomware-as-a-Service (RaaS) model remains irreversibly tarnished after the groups that pioneered this framework were exposed as being fraught with infighting, deception, lost profits, and compromised anonymity for their affiliates. Joint law enforcement actions over the last year have systematically impaired the resources ransomware actors depend on to operate. In the case of domestic threats, law enforcement efforts have even put a number of bad actors behind bars. While certain groups persist and new names continue to trickle in and out of the ransom-sphere, the era of having one or two definitive ransomware market “leaders” appears to be a distant motif. The landscape as of Q1-2025 is dominated by: (1) unaffiliated, lone operator extortionists, (2) a tranche of new-ish ransomware brands that blur the lines between traditional financially motivated cybercrime, espionage and hacktivism, and (3) a few surviving ransomware groups from a bygone era that still follow what we think of as a traditional ransomware playbook.
Q1-2025 was marked by several disparate but equally telling events. Just before Christmas, Clop unveiled their latest data theft campaign focused on the Cleo managed file transfer platforms, which garnered some initial notoriety due to the nature of the exploits, but seemed to lack the expected impact and monetization that was observed in past Clop campaigns, such as MOVEit (2023) and Accellion (2021).
In February, a slew of companies received physical ransom notes in the mail purporting to be from the well-known extortion group BianLian. The campaign was quickly identified as a phantom scam that was not affiliated with the real BianLian extortion group, but marked the first ransomware-related phantom extortion of its kind; this event further underscores the rise in phantom scams we’ve been tracking over the last 2 years as the victim landscape has narrowed and options for reliable and simple extortion monetization have diminished.
In March, a BreachForums actor announced a hack of Oracle Cloud Single Sign-On (SSO) environments, claiming to possess several million Java Key Store (JKS) files and encrypted Lightweight Directory Access Protocol (LDAP) credentials. While the scale of the attack generated significant attention, the threat actor responsible seemed uncertain as to how to handle or monetize the information, as evidenced in how they solicited assistance from their user base to help them decrypt the hashed credentials they had taken. The somewhat clumsy handling of the attack announcement is reminiscent of last year’s Snowflake hack, which also played out very publicly on the BreachForums stage rather than in the hushed and narrow confines of ransomware negotiation infrastructure.
Perhaps the most consequential event of the quarter however occurred in late February, when a trove of Black Basta Matrix chat logs was abruptly publicized and unceremoniously marked the closure of the infamous group. Black Basta emerged on the heels of the Conti ransomware gang collapse in early 2022, and quickly secured a share of the market, known for their effective initial access methods and devastating attacks on large enterprise targets. The leaked logs showcase internal communications between Black Basta affiliates that occurred over a twelve month period between September 2023-September 2024. The contents offer eye-opening insights on how the group approached victim targets, assessed risk, and navigated the delicate regulatory climate in the hopes of avoiding sanctions. Many of the themes identified in the logs highlight the mounting challenges ransomware actors face to maintain longevity and consistent profits. These sentiments were echoed more recently by another big game hunting group – Hunters International. According to researchers at Group-IB, Hunters leadership informed affiliates at the end of 2024 that the operation would soon be closing, citing “that development in the ransomware direction had become unpromising, low-converting, and extremely risky.”
The state of the union for ransomware in 2025 feels uncertain. While attacks are assuredly still occurring and new groups continue to spin up each month, the well-oiled ransomware machine that early RaaS groups built is plagued with complications that seem unlikely to resolve. To name a few:
-
Decryption tools are worse than they’ve ever been. A loss of consistent access to skilled developers has resulted in poorly written encryption code that cannot cleanly be reversed like it was in ransomware’s early days. The rate of attacks resulting in ransom payments has been declining for years, and being unable to trust that a payment will even result in a half-decent decryption tool further compounds this decline.
-
Sanctions concerns. The risk of sanctions looms large. As evidenced in the Black Basta chat logs, threat actors are keenly aware that hitting a single wrong target at the wrong time can put them on the fast track for unwanted regulatory scrutiny. If sanctioned, they will face immediate profit loss, a likely exodus of affiliates, and extended downtime as they weigh the pros and cons of trying to rebrand.
-
OPSEC concerns. Cyber extortion is not so anonymous anymore. The UK’s National Crime Agency (NCA) made sure to drive this point home during Operation Cronos, when they published the identities of key Lockbit affiliates. The threat actor behind the Snowfake campaign was identified and arrested in October. Numerous members of the Scattered Spider group have been taken into custody. The consequence of RaaS groups scaling operations to increase the volume of attacks and profits inadvertently scaled their personal footprints, leaving far more breadcrumbs for researchers and law enforcement to follow than existed in the early days. These continued unmaskings are eroding one of the most appealing attributes of cybercrime (its promise of anonymity), which will change the risk/reward calculus for existing and prospective affiliates.
-
Disruption of critical resources. RaaS models have dependencies. Without bulletproof hosting, money laundering, data brokers, etc., the enterprise ceases to function efficiently. Given the continued disturbance to all of the above, we expect affiliates have a growing reluctance to attach themselves to a business model whose supply chain is under constant threat of disturbance.
These circumstances have driven out many players from the old ransomware market. What remains is a patchwork of nomadic lone operators, state-linked actors who are experimenting in the cyber extortion space, and a dwindling contingent of ransomware affiliates who face mounting obstacles to retaining their thin share of the market. In past years, we’ve defined the state of ransomware by whichever attacks were most public or devastating; entering 2025, the data points that define the first quarter are a mashup of odd/clumsy events, and the unexpected demise of multiple market leading ransomware groups. While cyber extortion is here to stay for now, it looks very little like the extortion climate we have been dealing with for the last 5+ years. There is understandable speculation on whether ransomware stands to flourish if tensions between the United States and Russia start to ease and the agencies who have made great strides in disrupting ransomware are defanged. However, the kind of extortion groups that would have thrived under these conditions are beset with so many other challenges, it’s not clear that such conditions would actually enable them to prosper.
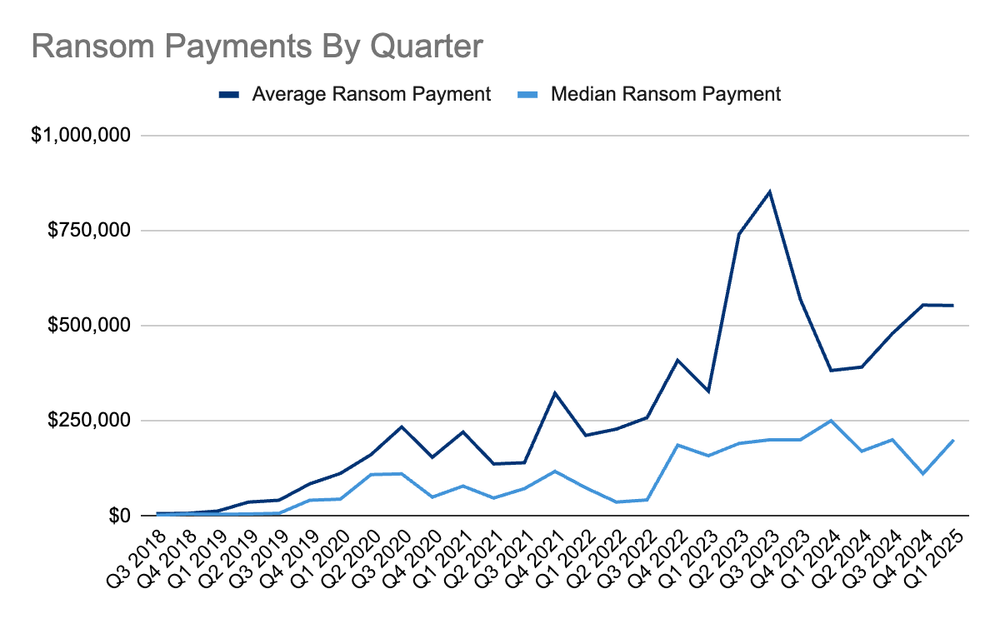
Average and Median Ransom Payment in Q1 2025

Average Ransom Payment
$552,777
-0.2% from Q4 2024
Median Ransom Payment
$200,000
+80% from Q4 2024
The median ransom payment in Q1 climbed to $200,000, which was an 80% increase from Q4 but exactly aligned with the Q3-2024 payment median (also $200,000), so well within expected limits. The average payment of $552,777 was almost identical to the average recorded in Q4. As expected, the highest payments were driven by decryption-motivated settlements to mitigate business interruption in the absence of valid backups. Only about one third of payments were driven by a desire to suppress the release of stolen data. Despite the big game hunting model that anticipates larger companies will pay larger ransoms, Coveware’s data shows it is not the company size or sector but rather the impact of the incident that drives costs.
Ransom Payment Rates in Q1 2025

The rate of companies that opted to pay a ransom, either to procure decryption keys or to suppress a threat actor from posting the breached data on their leak site, rose slightly in Q1 2025. We note that ransom payment rates have been bouncing between 25-35% for the trailing 6 quarters.

The rate of organizations that opted to pay a ransom SOLELY for the purposes of attempting to suppress the threat actor from releasing the breached data publicly, dropped slightly in Q1 2025, but remained in a normal bracket.
Most Common Ransom Variants in Q1 2025
| 1 | Akira | 14% | – |
| 1 | Ransomhub | 14% | +1 |
| 2 | Lone Wolf | 9% | +1 |
| 3 | Qilin | 8% | New in Top Variants |
| 4 | Medusa | 5% | – |
| 4 | Fog | 5% | -3 |
| 4 | Inc Ransom | 5% | New in Top Variants |
Market Share of the Ransomware attacks
At the end of Q1-2025, Akira and RansomHub were the only name brand groups to hold double digit market share. However, at the time of writing, we are monitoring the abrupt disappearance of RansomHub after their infrastructure disconnected on/around April 2, 2025. While the disruption followed recent reporting linking RansomHub to the sanctioned enterprise known as Evil Corp, it remains unclear as to whether this was a contributing factor to the group’s disappearance. As this is a developing event, we will reserve further speculations for a later report.
Most significantly, we find that unaffiliated lone extortionists (“lone wolf” actors) continue to hold a significant presence in our data. Readers may recall this was also a finding of note in Coveware’s Q2-2024 report, which we attributed to the sharp distrust that developed in the affiliate community following the revelation of these groups’ unfair practices and vulnerability to law enforcement. It was unclear at the time whether this perception was temporary, but with twelve months of hindsight and lone wolf actors still operating at steady volume, it would seem the impact was more permanent.
Most Common Ransomware Initial Attack Vectors in Q1 2025

During the first quarter of 2025, ransomware actors increasingly exploited known CVE’s as the initial ingress method of their attacks. Among the most targeted were:
-
CVE-2025-0282: A critical stack-based buffer overflow vulnerability in Ivanti Connect Secure VPN appliances, allowing unauthenticated remote code execution.
-
CVE-2025-23006: A deserialization flaw in SonicWall SMA1000 appliances, enabling unauthenticated attackers to execute arbitrary OS commands via the management interface.
-
CVE-2025-22457: A buffer overflow vulnerability in Ivanti Connect Secure VPN appliances, exploited in the wild to deploy malware.
-
CVE-2024-41713 and CVE-2024-55550: Path traversal vulnerabilities in Mitel MiCollab systems, actively exploited to gain unauthorized access.
-
CVE-2024-0012: A vulnerability in Palo Alto Networks PAN-OS, leading to unauthorized access and potential system compromise.
These vulnerabilities were frequently leveraged by ransomware groups, who will often employ multiple tactics such as phishing campaigns and exploiting unpatched systems to gain initial access. The Cybersecurity and Infrastructure Security Agency (CISA) has included these CVEs in its Known Exploited Vulnerabilities Catalog, emphasizing the critical need for timely patching and system updates to mitigate the risk of ransomware attacks.
Most Common Tactics, Techniques and Procedures Threat Actors used in Q1 2025

Exfiltration [TA0010]: Kicking off 2025, Exfiltration retained its top spot from Q4 2024, appearing in 71% of cases (a decrease from 87% in Q4). This is a continued sign that data theft is a primary objective for most threat actors and is not just a precursor to encryption-based attacks. In Q1, threat actors favored the use of MEGASync, Rclone, and WinSCP. There was also an uptick in abusing temporary file sharing services like file.io, bashupload.com or easyupload.io to offload stolen data.
Lateral Movement [TA0008]: Lateral Movement was observed in 67% of cases in Q1, confirming it is still a key phase in an attack, as adversaries continue to focus on domain wide impact. Common techniques include the use of internal Remote Desktop Protocol (RDP) to jump from host to host, as well as PsExec and secure shell (SSH). Notably, OpenSSH and PuTTy were used by ransomware threat actors to target virtualized infrastructure, especially VMware ESXi hots, to directly deploy ransomware at the hypervisor level.
Defense Evasion [TA0005]: Defense Evasion was present in 60% of cases in Q1, highlighting the growing necessity by threat actors to disable or bypass anti-virus or Endpoint Detection & Response (EDR) solutions to successfully deploy ransomware. Techniques used for defense evasion include uninstalling/disabling security software or services, clearing Windows event logs, or using custom, obfuscated scripts to avoid detection. Threat actors were also observed using Bring Your Own Vulnerable Driver (BYOVD) techniques to tamper with legitimately signed, but vulnerable drivers to disable protections or escalate privileges. These techniques indicate defense evasion is now a standard prerequisite for successful ransomware execution.
Impact [TA0040]: Impact remains in the top 5, where ransomware, data destruction or tampering with infrastructure was observed in 58% of cases (up from 45% in Q4). However, this ranking understates its true significance, as confirmed ransomware encryption occurred in 91% of our Q1 cases. This activity centered on VMware ESXi environments, where threat actors locked administrators out of the ESXi console via password tampering, making detection and recovery more difficult. In many cases, victims were forced to reinstall ESXi to regain access to datastores, inadvertently destroying forensic artifacts in the process. This is also compounded by low ransom payment rates, as organizations often deprioritize forensic efforts when payments are not made.
Command and Control [TA0011]: Command and Control (C2) was seen in 51% of our cases, reinforcing the reliance of threat actors on persistent access infrastructure to orchestrate attacks. Many adversaries are still leveraging legitimate Remote Monitoring and Management (RMM) tools such as AnyDesk, SimpleHelp, and Atera to better go undetected. Organizations must enhance their monitoring capabilities to identify unusual activity associated with these tools, as well as other RMM tooling, and consider both application and network controls to mitigate the risks associated with unauthorized use of legitimate software.
Most Common Industries Impacted by Ransomware in Q1 2025

Ransomware attacks in Q1 2025 opportunistically impact several specific industries, with healthcare, professional services, and the public sector suffering the highest rates of incidents. Healthcare organizations accounted for 15.4% of all ransomware cases, reflecting the sector’s ongoing vulnerability due to critical operations and often outdated infrastructure. Professional services, including legal, accounting, and consulting firms, made up 14.4% of incidents, highlighting the high value of sensitive client data to threat actors. Meanwhile, the public sector—including government agencies and educational institutions—represented 12.5% of total ransomware attacks, underscoring the persistent risk to essential public services.
Size of Organizations Impacted by Ransomware in Q1 2025

Median Company Size
228
-20% from Q4 2024
In Q1 2025, ransomware attacks disproportionately affected small and mid-sized organizations. The median size of a victimized organization was just 228 employees, reinforcing that the ransomware groups with the most market share tend to impact these smaller and middle market companies with limited cybersecurity resources. Organizations with 11–100 employees represented the largest share of victims, accounting for 35.6% of attacks, while companies with 101–1000 employees made up 32.7% of incidents. This trend highlights that smaller enterprises, which may lack the robust defenses of larger corporations, remain prime targets for ransomware operations.

While small to mid-sized companies have suffered the brunt of ransomware impact over the last several quarters, we suspect there will be a resurgence of impact to the large enterprise market if we continue to see a trend of state actors from China and North Korea step into the extortion space (which has historically been dominated by Russian-based groups). In just the last six months, researchers have identified links between North Korean state actors and not one but two ransomware groups: PLAY and Qilin. If this trend persists, and state sponsored crime starts to use ransomware either to directly fund their regimes, or as a cover to hide their true intrusion motives, we may see the first measurable increase in attacks that are truly targeted towards companies of a certain size and industry vertical. This would be a stark departure from the purely opportunistic nature of ransomware attacks that has existed for the last 10+ years.
*** This is a Security Bloggers Network syndicated blog from Blog | Latest Ransomware News and Trends | Coveware authored by Bill Siegel. Read the original post at: https://www.coveware.com/blog/2025/4/29/the-organizational-structure-of-ransomware-threat-actor-groups-is-evolving-before-our-eyes