Enterprises spend billions of dollars annually on cybersecurity products to keep them from getting hacked. And yet, the hacks keep coming – and they’re getting worse. Why?
A new report out from ReversingLabs* a malware analysis and software supply chain security firm, has an answer: because the open source and commercial software and services those enterprises run on are full of security issues that make them easy prey for malicious actors.
ReversingLabs’ 2025 Software Supply Chain Security Report, released on Wednesday, finds that security flaws in commercial and open source supply chains are epidemic, as malicious actors pivot to target supply chains including those supporting cryptocurrency and AI applications in a play to gain access to sensitive data and IT assets.
Commercial Code: There’s Insecurity in Obscurity
As part of their investigation, ReversingLabs researchers analyzed 30 closed source, commercial software binaries including commercial and open-source operating systems, web browsers, and virtual private network (VPN) software.
RL’s experts scanned client executables as well as installer and setup files for the applications in question using the company’s Spectra Assure platform. They found many of the scanned packages received a failing from Spectra, indicating the presence of serious security risks. For example, the survey of commercial software binaries included 20 versions of VPN clients from six different enterprise vendors. Of those: seven of the 20 VPN packages contained one or more software vulnerabilities that are considered “patch- mandated,” meaning that they are being actively exploited by malware.
Though less talked about than open source risks, the risks hiding in commercial binaries pose a much more direct threat to the security of sensitive enterprise networks and data, given the heavy reliance of organizations on proprietary, closed source commercial software.
“They say the world runs on open source,” observes Saša Zdjelar, ReversingLabs Chief Trust Officer. “But your business runs on commercial software.”
In Open Source Software: Popularity Doesn’t Equal Security
The risks weren’t limited to commercial binaries, however. RL researchers also analyzed 30 widely used npm, PyPI, and RubyGems packages for the report – looking for risks that might make them targets for malicious actors. They found that large numbers of critical and exploitable flaws lurk in the latest versions of open-source packages that account for 650 million lifetime downloads – and tens of millions of weekly downloads across the three package managers.
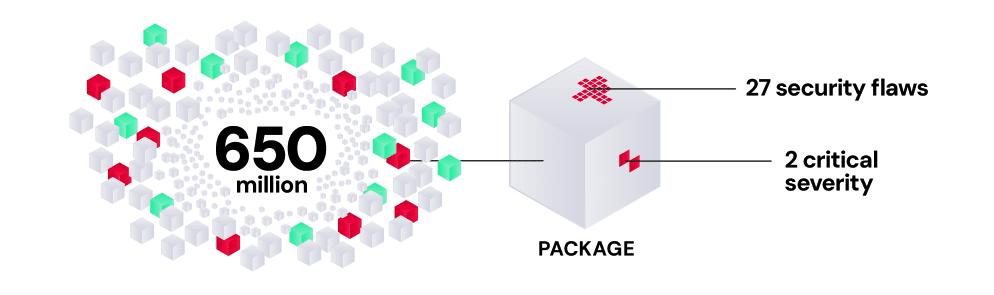
Across the 30 packages surveyed, researchers detected a median of 27 security flaws per package (avg. 68), including 2 critical-severity flaws (avg. 2). Among the open source packages on the npm package manager, for example, RL researchers discovered 10 packages containing patch-mandated security flaws. Together, those 10 npm packages account for more than 61,000 weekly downloads and 18 million total downloads since 2021.
Typical of them was turbo-linux-arm, a platform-specific binary for running Turborepo, a build system for JavaScript and TypeScript codebases on Linux distributions based on the Debian and ARM 64 architectures. It sports more than 10,000 weekly downloads and 9.5 million lifetime downloads.
Despite that popularity, turbo-linux-arm hides serious security holes that impact dependent applications. RL’s scan of the latest version of the turbo-linux-arm package (1.4.7) detected 41 distinct vulnerabilities, with four rated “critical” and 24 rated “high” severity dating back to 2021. All the identified vulnerabilities had patches available, but those have not been applied by the maintainers.
Code Rot, Leaked Secrets And Other Deadly Sins of Software Producers
Contemporary software risks stretch well beyond “common vulnerabilities and exposures” (CVEs) – the focus of the information security community for the last 25 years. Security issues uncovered by the RL researchers include:
- The failure by software producers to “harden” their code by properly implementing security features like address space layout randomization (ASLR)
- The unintentional exposure of developer “secrets” like encryption and API keys or hard coded credentials is another source of supply chain risk. RL researchers saw instances of leaked developer secrets jump 12% across the three main open source platforms compared with the previous year.
- Code rot – a term that describes developers’ continued reliance on old, outdated or poorly maintained open source and third party code. Code rot was common in the open source and commercial packages RL researchers analyzed.
That lack of urgency among publishers and maintainers of proprietary and open source software is a common theme in the RL Software Supply Chain Security Report. RL researchers analyzed Torchvision, an open source module created by AI engineers at Meta that is in the top 1% of all Python packages, with more than 3.4 million weekly downloads. The package is actively maintained, with 50 versions dating back eight years and 10 releases between January 2024 and January 2025 alone.
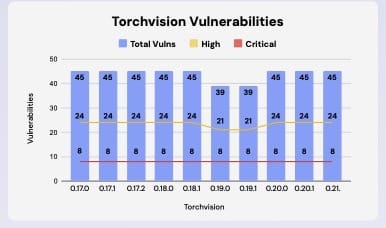
But recent versions of Torchvision received a failing grade from RL’s Spectra Assure analysis, with 45 vulnerabilities identified in the latest, scanned version of the package, eight with a “critical-” severity rating and 24 with a “high-” severity rating, as well as one that is considered “patch mandated.” Those numbers have held steady over the last 10 released versions of Torchvision, dating back to 2023.
Attacks on Crypto: A Sign of What’s to Come
What does the future look like for enterprises struggling to navigate a landscape of vulnerable commercial and open source code? RL researchers point to the nearly two dozen (23) supply chain attacks on cryptocurrency applications and infrastructure in 2024 as evidence of what’s to come for other industries as malicious actors lean into supply chain vulnerabilities to further malicious campaigns.
An example cited in the report is the hack of the npm package @solana/web3.js, a JavaScript API for use with the Solana blockchain platform that ranks among the top 10,000 projects in the npm community, with more than 3,000 dependent projects and 400,000 weekly downloads.
Supply chain hackers implanted malicious functions in two versions of the package (1.95.6 and .7) in December. A subsequent GitHub advisory warned that “any computer that has this package installed or running should be considered fully compromised.” with “all secrets and keys stored on that computer” potentially exposed to malicious actors.
The lesson? Software supply chain risks are evolving, with sophisticated and long-horizon “hands-on-keyboard” campaigns taking place alongside broader, automated campaigns seeking access to sensitive developer systems and environments.
(*) The author of this article is an employee of ReversingLabs and contributed to the creation of the 2025 Software Supply Chain Security Report.

